Hacker Course Buffer Overflow - A Practical Example (with Exploit)
System Hacking : Buffer Overflow , Privilege Escalation & Maintaining Access Made EasyПодробнее
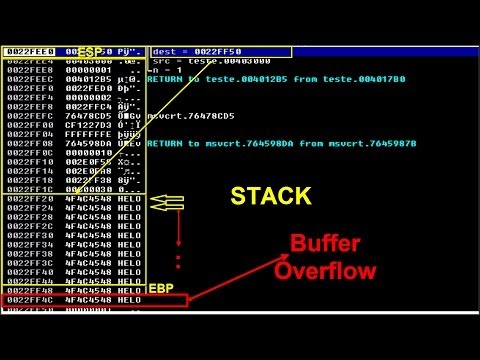
How Overflow Exploits Can Be Carried Out: A Practical ExampleПодробнее

10: Bypassing Stack Canaries (leak + write) - Buffer Overflows - Intro to Binary Exploitation (Pwn)Подробнее

Exploiting Return Oriented Programming (ROP) tutorial - Binary Exploitation PWN101Подробнее

Buffer OverflowПодробнее

Hacker Course Buffer Overflow A Practical Example with ExploitПодробнее
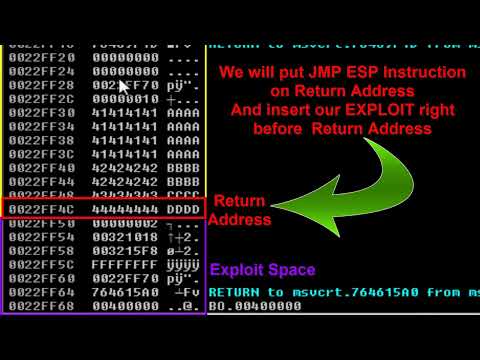
why do hackers love strings?Подробнее

Get Started with GDB and Buffer Overflow Hacking!Подробнее

0: Intro/Basics/Setup - Buffer Overflows - Intro to Binary Exploitation (Pwn)Подробнее

Buffer Overflow Attack Example | Exploiting BinaryПодробнее
Practical Of Buffer Overflow On Website 1Подробнее
Running a Buffer Overflow Attack - ComputerphileПодробнее
Binary Exploitation Buffer overflowПодробнее
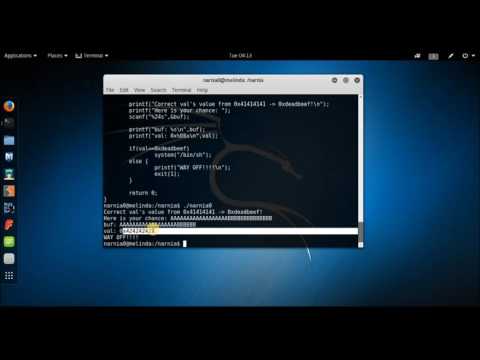
How to exploit a buffer overflow vulnerability - PracticalПодробнее
Lec40 Exploiting Buffer Overflow Vulnerability Part-III (Arif Butt @ PUCIT)Подробнее

Practical exploitation of a Buffer Overflow vulnerable C programПодробнее

Real World Hacking Penetration Testing Part-24 (Binary Exploitation - Buffer overflow attack)Подробнее

How to exploit a buffer overflow vulnerability - TheoryПодробнее