Practical exploitation of a Buffer Overflow vulnerable C program

Understanding Buffer Overflow Vulnerabilities in C CodeПодробнее

Buffer Overflow CTF Handbook CTF101Подробнее

Buffer overflow is not rocket scienceПодробнее
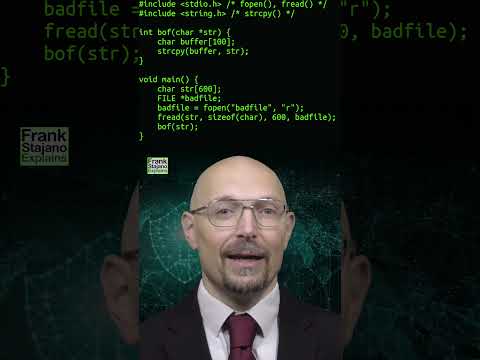
How to Exploit a Buffer Overflow to Bypass Username Validation in C CodeПодробнее

why do hackers love strings?Подробнее

Buffer Overflow CTF Handbook CTF101Подробнее

02 binary exploitation format string vulnerabilityПодробнее

4 5 integer overflow dive into systemsПодробнее

Buffer Overflow Vulnerability Exploit | Malayalam | Using Return PointerПодробнее
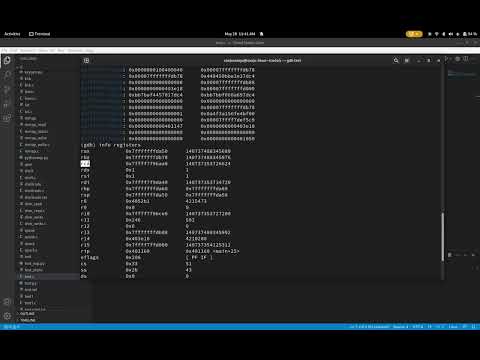
7: Format String Vulnerabilities (printf) - Buffer Overflows - Intro to Binary Exploitation (Pwn)Подробнее

Buffer Overflow Attack Example | Exploiting BinaryПодробнее
How to exploit a buffer overflow vulnerability | Full PracticalПодробнее

Buffer OverflowПодробнее

3: Return to Win (Ret2Win) - Buffer Overflows - Intro to Binary Exploitation (Pwn)Подробнее

buffer overflow vulnerability - Practical (ONLY FOR EDUCATIONAL PURPOSES )Подробнее
Lec38 Exploiting Buffer Overflow Vulnerability Part-I (Arif Butt @ PUCIT)Подробнее

COS330 Buffer Overflow Practical AssignmentПодробнее
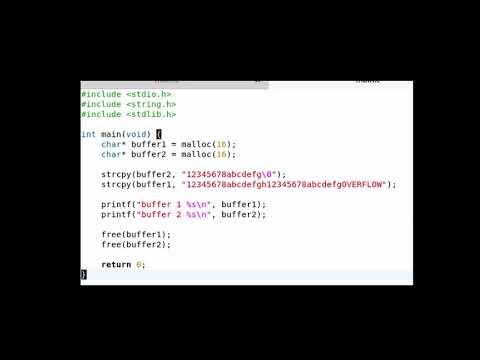
Buffer Overflow Attack - Simple, Practical, Effective + ExplanationПодробнее

0: Intro/Basics/Setup - Buffer Overflows - Intro to Binary Exploitation (Pwn)Подробнее
