Real World Hacking Penetration Testing Part-24 (Binary Exploitation - Buffer overflow attack)

Day 8 | Web Penetration Testing full course in 90 days | SQL Injection | Rayofhope | Ethical HackingПодробнее

Practical Buffer Overflow on unknown Server | OSCP like exploitation | x86Подробнее

Buffer Overflow Attack & Penetration Testing - TryHackMe!Подробнее

real world penetration testing : buffer overflowsПодробнее
024 Binary Exploitation Buffer overflow attackПодробнее
Binary Exploitation vs. Web SecurityПодробнее

Exploiting Simple Buffer Overflows on Win32 : JMPCALL EAX TechniqueПодробнее
Penetration Testing - Buffer Overflow and Malware backdoor - learn Penetration TestingПодробнее
Video 2 - Basic Exploit Development - Direct Buffer OverflowПодробнее

CTF | OverTheWire | Wargames | Narnia | Level 3 | Exploiting Buffer Overflow to Gain AccessПодробнее

Buffer Overflow tested on real applicationПодробнее
Hack Remote Windows PC with Watermark master buffer overflow exploit Kali LinuxПодробнее
Buffer Overflow AttackПодробнее

exploit strcpyПодробнее
What is buffer overflow?Подробнее
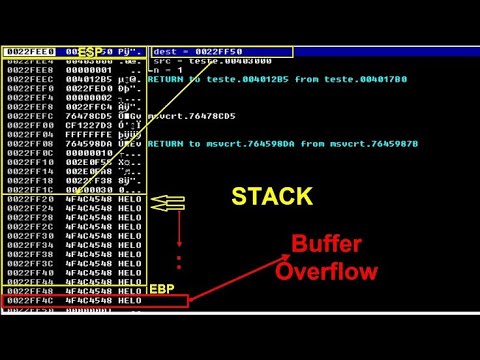
CEH v6 Module 24 by QuickCert: Buffer OverflowsПодробнее

01 System Hacking - Buffer Overflow AttackПодробнее