Log4Shell & Log4j Explained - ThreatWire
Easy Log4J Exploit Detection with CanaryTokens | HakByteПодробнее

Log4Shell & Log4j Explained - ThreatWireПодробнее

How Hackers Exploit Log4J to Get a Reverse Shell (Ghidra Log4Shell Demo) | HakByteПодробнее
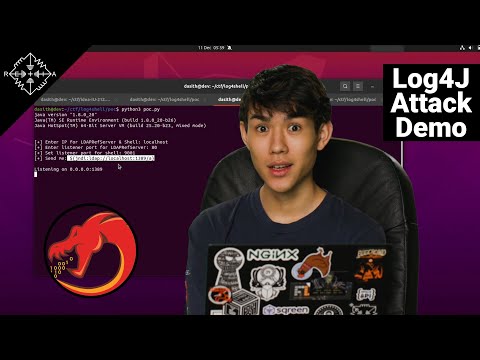
Log4j Vulnerability (Log4Shell) Explained // CVE-2021-44228Подробнее

Log4j (CVE-2021-44228) RCE Vulnerability ExplainedПодробнее
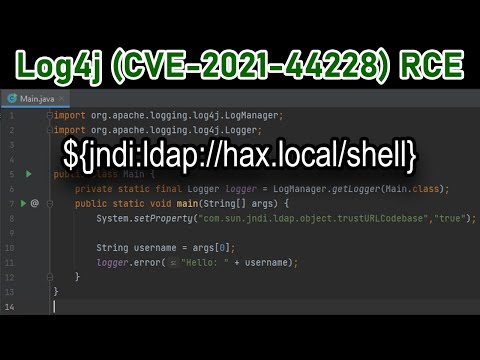
Log4J Vulnerability (Log4Shell) Explained - for Java developersПодробнее

What is the Log4j Vulnerability and How to Protect Against ItПодробнее

Log4J Exploit Explained: How it Works, In-Depth Examples, Mitigation, etc. | Log4Shell VulnerabilityПодробнее

Log4J Security Vulnerability: CVE-2021-44228 (Log4Shell) - in 7 minutes or less (PATCH NOW!)Подробнее

Apache Log4j: The Exploit that Almost Killed the InternetПодробнее

Log4j vulnerability explainedПодробнее

Log4J & JNDI Exploit: Why So Bad? - ComputerphileПодробнее

Log4J and JNDI Exploit Explained - Log4ShellПодробнее

Log4J - CVE 2021-44228 (Log4Shell) - Exploitation & MitigationПодробнее

Exploits Explained: How Log4j, Buffer Overflows and Other Exploits WorkПодробнее
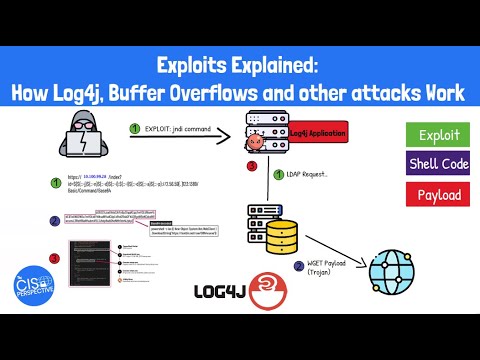
SheHacksPurple: Log4J explained for Software Developers and AppSec FolksПодробнее
