What Is Privileged Account and Session Management & How Can It Benefit Your Business?
What Is Privileged Account and Session Management & How Can It Benefit Your Business?Подробнее

AppManagEvent 2023 session - Privileged Access Management for Today’s Cyber Threats - Dirk SchräderПодробнее

CyberArk Tutorial | CyberArk Training | CyberArk Course | CyberBrainerПодробнее
Privileged Account and Session ManagementПодробнее

NetIQ Privileged Account Manager: popular use casesПодробнее
Privileged Access Management: Beyond Vaulting - Brett Jones, DelineaПодробнее

Protecting your most valuable assets with NetIQ PAMПодробнее

Platform Management for CyberArk PAM DemoПодробнее
Identity Centric Webinar-The Integrations - Session 3: Integration with Privileged Access ManagementПодробнее

LEVELING THE PLAYING FIELD: Privileged Access Management in CybersecurityПодробнее

Best Practices for Privileged Access & Secrets Management in the CloudПодробнее

Manage "Securing Privileged Accounts - "A Hacker's Top Target" in an Organization"Подробнее

Extend Your Identity Investment to Privileged AccountsПодробнее

AWS re:Invent 2016: IAM Best Practices to Live By (SAC317)Подробнее

Privileged Access Management It’s for Applications tooПодробнее

Privileged Access Management: Not Just a Credential VaultПодробнее
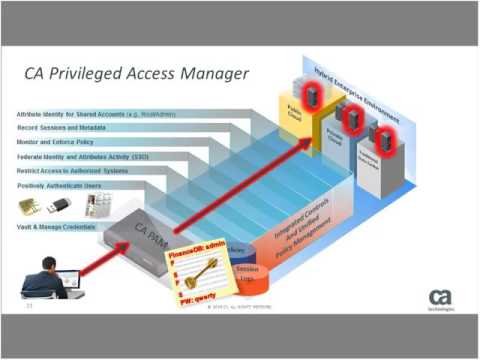
Ruling the Kings of Keys | Managing Privileged AccountsПодробнее

2014 Cyber Security Session 12 - Privileged User ManagementПодробнее
