USENIX Security '14 - Blanket Execution: Dynamic Similarity Testing for Program Binaries
USENIX Security '14 - Blanket Execution: Dynamic Similarity Testing for Program BinariesПодробнее
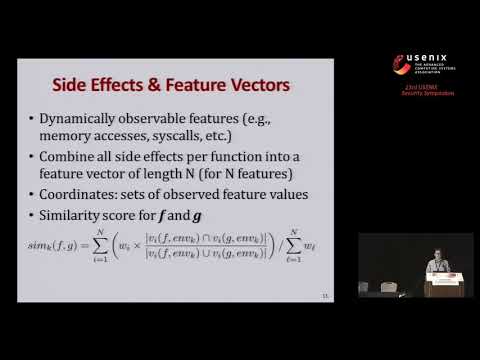
USENIX Security '24 - D-Helix: A Generic Decompiler Testing Framework Using Symbolic DifferentiationПодробнее

USENIX Security '17 - BinSim: Trace-based Semantic Binary Diffing...Подробнее

USENIX Security '22 - SYMSAN: Time and Space Efficient Concolic Execution via Dynamic Data-flowПодробнее

USENIX Security '20 - Symbolic execution with SymCC: Don't interpret, compile!Подробнее

USENIX Security '14 - X-Force: Force-Executing Binary Programs for Security ApplicationsПодробнее

USENIX Security '18 - Precise and Accurate Patch Presence Test for BinariesПодробнее

USENIX Security '22 - Arbiter: Bridging the Static and Dynamic Divide in Vulnerability Discovery...Подробнее

USENIX Security '15 - Under-Constrained Symbolic Execution: Correctness Checking for Real CodeПодробнее

USENIX Security '20 - HALucinator: Firmware Re-hosting Through Abstraction Layer EmulationПодробнее

USENIX Security '18 - Formal Security Analysis of Neural Networks using Symbolic IntervalsПодробнее

USENIX Security '24 - Inference of Error Specifications and Bug Detection Using Structural...Подробнее

USENIX Security '22 - DnD: A Cross-Architecture Deep Neural Network DecompilerПодробнее

USENIX Security '24 - Neural Network Semantic Backdoor Detection and Mitigation: A Causality-Based..Подробнее

USENIX Security '20 - PHMon: A Programmable Hardware Monitor and Its Security Use CasesПодробнее

USENIX Security '17 - Neural Nets Can Learn Function Type Signatures From BinariesПодробнее

USENIX Security '18-Inception: System-Wide Security Testing of Real-World Embedded Systems SoftwareПодробнее

USENIX Security '21 - Phishpedia: A Hybrid Deep Learning Based Approach to Visually IdentifyПодробнее
