Unlocking Security: A Deep Dive into Zero-Trust Architecture with Tom Madsen's New Book!
Unlocking Security: A Deep Dive into Zero-Trust Architecture with Tom Madsen's New Book!Подробнее

Cybersecurity and Zero TrustПодробнее

Zero Trust Part 2: ArchitectureПодробнее
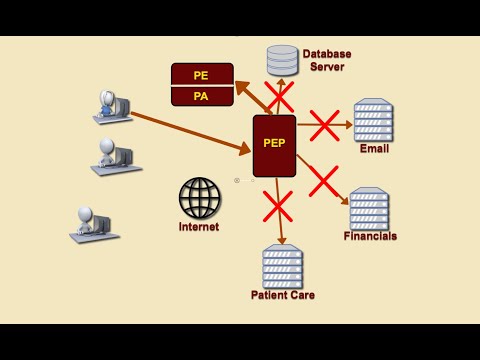
Overview of Zero Trust ArchitecturesПодробнее

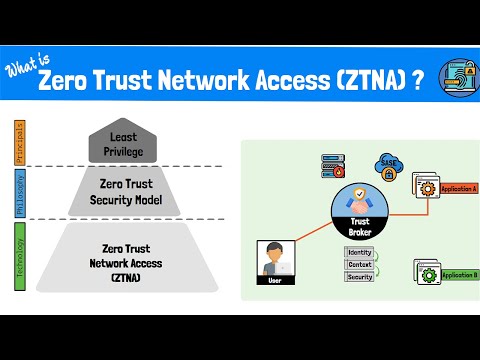
What is Zero Trust Network Access (ZTNA)? The Zero Trust Model, Framework and Technologies ExplainedПодробнее
What is zero trust security?Подробнее

Zero Trust Explained in 4 minsПодробнее
CSM Podcast: Zero Trust with Tom MadsenПодробнее

Going Beyond Identity: A Deep Dive into Zero Trust Security | Analyst Chat 233Подробнее

Zero Trust Security Model: The Future of Cybersecurity Explained 🔒Подробнее

What is Zero Trust Architecture?Подробнее

Navigating the Path to Zero Trust in 2024Подробнее

Why Implement Zero TrustПодробнее

Introducing the Zero Trust Security courseПодробнее

ETSI Security Conference 2023: Exploring Zero Trust Architecture with Dr. Galina PildushПодробнее
