Talkie Pwnii #1: Exploiting SQL LIKE Operator & Command Injection Regex Bypass
Talkie Pwnii #1: Exploiting SQL LIKE Operator & Command Injection Regex BypassПодробнее

Talkie Pwnii #2: Exploiting second order SQL injection to extract dataПодробнее

Bypass SQL Filters & Get SQL Injection With These Quick TipsПодробнее

SQL Injection 101: Exploiting VulnerabilitiesПодробнее

Hacking into the Bank with SQL MapПодробнее
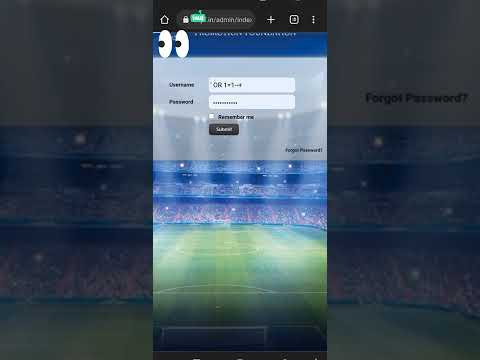
ADMIN LOGIN AUTHENTICATION BYPASS USING SQLi(SQL Injection) Payloads #sql #injection #sqli #bypassПодробнее
Kids vs. MALWARE!!Подробнее

What Is SQL Injection?Подробнее
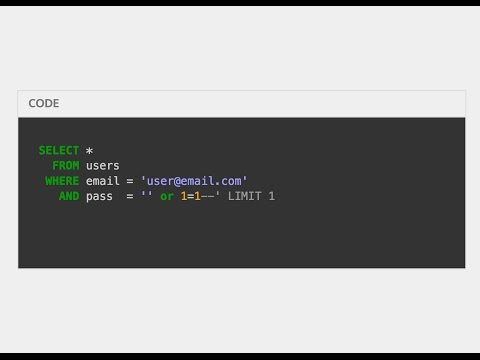
Dangerous Codes: SQLiПодробнее
what is an SQL Injection?Подробнее

SQL Injections are scary!! (hacking tutorial for beginners)Подробнее

Exploit SQL injection To Bypass LoginПодробнее

Bypassing SQL Filters (picoCTF Web Gauntlet)Подробнее