Proactive Threat Detection & Automated Threat Hunting in the Era of Security Data Lakes: Part 1
Proactive Threat Detection & Automated Threat Hunting in the Era of Security Data Lakes: Part 1Подробнее

Cybersecurity Threat Hunting ExplainedПодробнее

Proactive Threat HuntingПодробнее

1. Security Detection and Threat HuntingПодробнее

PART 1 - ICS Proactive Defense: Leveraging Operational Threat hunting for ResilienceПодробнее

Splunk Security Investigations, Part 1: Threat DetectionПодробнее

Introduction to Cyber Threat Hunting : SOCПодробнее
Automation, Data Lakes & Addressing the Talent Shortage in Cyber SecurityПодробнее

Proactive threat detection and prevention for your network.Подробнее

Threat Hunting in the Modern SOC with SplunkПодробнее

Data Anomaly Driven Web Threat HuntingПодробнее

Finding the Balance in Security Automation - SANS Threat Hunting Summit 2018Подробнее

Glitterbomb Trap Catches Phone Scammer (who gets arrested)Подробнее

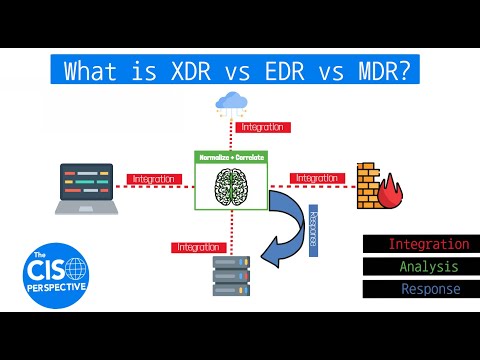
What is XDR vs EDR vs MDR? Breaking down Extended Detection and ResponseПодробнее
SentinelOne Singularity XDR - Welcome to the Age of OneПодробнее
