HTTP 2 request splitting via CRLF injection

24.11 Lab: HTTP/2 request splitting via CRLF injection - Karthikeyan Nagaraj | 2024Подробнее

Laboratorio "HTTP2 request splitting via CRLF injection"Подробнее

Lab: HTTP/2 request splitting via CRLF injectionПодробнее

Lab: HTTP/2 request smuggling via CRLF injectionПодробнее

HTTP 2 request smuggling via CRLF injectionПодробнее

HTTP 2 request smuggling via CRLF injectionПодробнее

Web Security Academy | Request Smuggling | 14 - HTTP/2 Request Splitting via CRLF InjectionПодробнее

Web Security Academy | Request Smuggling | 13 - HTTP/2 Request Smuggling via CRLF InjectionПодробнее

HTTP2 request splitting via CRLF injectionПодробнее

PortSwigger Lab: HTTP/2 request smuggling via CRLF injectionПодробнее

$200 - CRLF Injection - Http Response Splitting on www.exness.com | #HackerOneПодробнее

$200 Bounty - CRLF Injection - Http Response Splitting | www.exness.com | #HackerOne | #mufazmiПодробнее
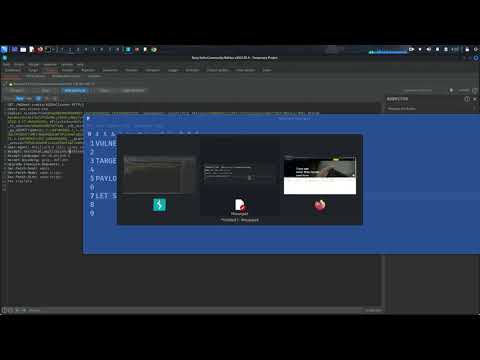
🎬 Demo: HTTP Request Smuggling HTTP/2 to HTTP/1.1Подробнее

Exploiting HTTP request smuggling to bypass front-end security controls, CL.TE vulnerabilityПодробнее
HTTP request smuggling, confirming a CL.TE vulnerability via differential responsesПодробнее

HTTP request smuggling, obfuscating the TE headerПодробнее
HTTP request smuggling, basic TE.CL vulnerabilityПодробнее

HTTP request smuggling, basic CL.TE vulnerabilityПодробнее
HTTP/2 request splitting via CRLF injectionПодробнее
