|| How Hacker's Exploit SQL Injection & Bypass Two-Factor Authentication (2FA) ||
|| How Hacker's Exploit SQL Injection & Bypass Two-Factor Authentication (2FA) ||Подробнее
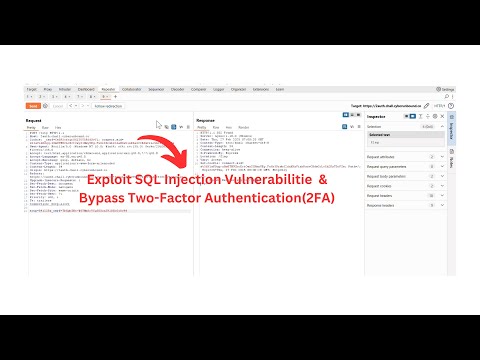
Exploit SQL injection To Bypass LoginПодробнее

How Hackers Bypass Logins with SQL Injection - Live DemoПодробнее
SQL Injections are scary!! (hacking tutorial for beginners)Подробнее

Unlocking SQL Injection Login Bypass: A Hacker's Trick Exposed!Подробнее
how hackers bypass login pages!Подробнее

Authentication Bypass via Response manipulation Vulnerability Live Website #Bugbounty #POC || 2022Подробнее
Hacking Two Factor Authentication: Four Methods for Bypassing 2FA and MFAПодробнее
Hackers Discover a Method to Bypass Two-Factor AuthenticationПодробнее
Hacking into the Bank with SQL MapПодробнее
Hackers Bypass Google Two-Factor Authentication (2FA) SMSПодробнее
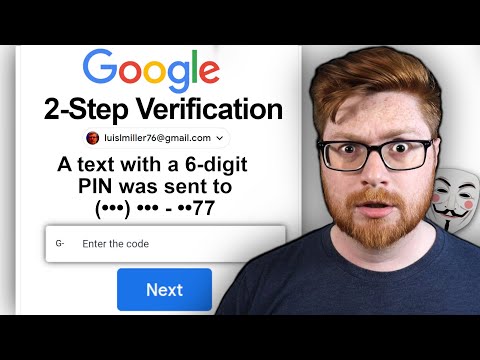
How To Bypass Two-Factor Authentication | How Hackers Bypass Two-Factor Authentication #2FAHackingПодробнее

Make your Gmail account even more secure with account recovery and 2-step authentication #shortsПодробнее
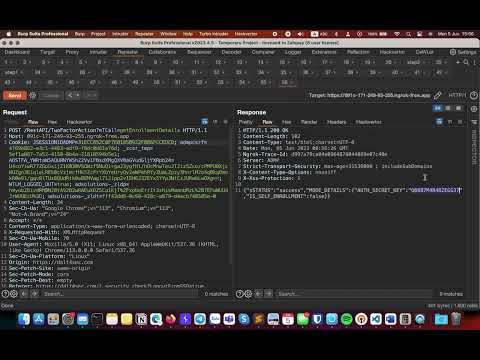
BYPASS 2FA Vulnerability - PoCПодробнее
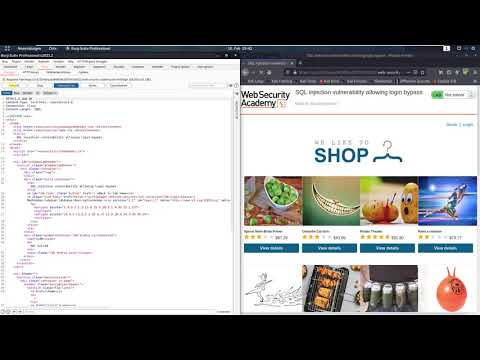
SQL injection vulnerability allowing login bypass (Video solution, Audio)Подробнее
SQL Injection Attack: How Hackers Exploit & How to Stay Safe! 🚨Подробнее

how hackers bypass 2 step verificationПодробнее

SQL Injection: Hack Any Website (Step-by-Step Guide)Подробнее
Two Factor Authentication (2FA) Bypass Hacking for LinkedIn (Joe the Hacker)Подробнее

How hackers bypass 2FAПодробнее

How To Bypass Two-Factor Authentication | How Hackers Bypass Two-Factor Authentication #2FAHackingПодробнее