Exploiting - SSH PuTTY login Brute-Force - Cyber Security Compliance 2023

How Hackers Could Brute-Force SSH Credentials to Gain Access to ServersПодробнее
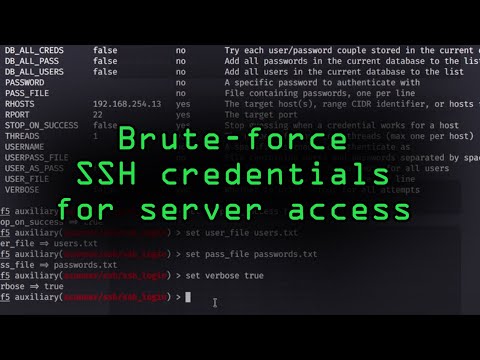
How Easy Is It For Hackers To Brute Force Login Pages?!Подробнее

Hacking into Android in 32 seconds | HID attack | Metasploit | PIN brute force PoCПодробнее

When you first time install Kali linux for hacking 😄😄 #hacker #shortsПодробнее

How hackers brute force FTP service #cybersecurity #hacking #cyber #security #hacktheplanetПодробнее

Python SSH Login Brute Force - Ethical Hacking and Network SecurityПодробнее
How to HACK Website Login Pages | Brute Forcing with HydraПодробнее
Brute Forcing An iPhone 5… #technologyПодробнее

Password Cracking with HydraПодробнее

How Hackers Bruteforce Login Pages of Any Website!Подробнее

Unlock Any Device By Termux #short #youtubeshorts #trending #viralПодробнее
Ten Minute Tutorials : How to Brute Force SSH!Подробнее

SQL Injection 101: Exploiting VulnerabilitiesПодробнее

A Day in the Life of Cyber Security | SOC Analyst | Penetration Tester | Cyber Security TrainingПодробнее

The #1 Hacking OS #shortsПодробнее

Normal people vs programmer vs hackers compression #codingПодробнее
How to Hack SMTP Username and Password | Metasploitable v2 2023Подробнее
How To Hack and Exploit Port 22 SSH Metasploitable 2 - Home Hacking Lab Video 6Подробнее
