Python SSH Login Brute Force - Ethical Hacking and Network Security
How to Hack Passwords Using Hydra!Подробнее
HYDRA | Brute-Forcing Tool | ExplainedПодробнее

How Hackers Bruteforce Login Pages of Any Website!Подробнее

How To Hack Login Services And Brute Forcing With Hydra Kali Linux Tools - 2023Подробнее

PYTHON FOR PENETRATION TESTING 6 | SSH AND FTP SCRIPTS | BRUTE FORCING SCRIPTS | AUTOMATING SSHПодробнее

How to HACK Website Login Pages | Brute Forcing with HydraПодробнее
hacking every device on local networks - bettercap tutorial (Linux)Подробнее

How Hackers Login To Any Websites Without Password?!Подробнее

Brute Force Attack Explained in Hindi l Information and Cyber SecurityПодробнее

Brute Force(complete tutorial ) and system accessing using ssh | Ethical Hacking | Malayalam |Подробнее

Is your Router Hackable ? (Gaining Access To Routers)Подробнее
How to use Hydra to brute force login pagesПодробнее

How Easy Is It For Hackers To Brute Force Login Pages?!Подробнее

How to Brute force ssh login using Hydra (Hindi) | Pentesting SimplifiedПодробнее

Hacking into Android in 32 seconds | HID attack | Metasploit | PIN brute force PoCПодробнее

How Hackers Could Brute-Force SSH Credentials to Gain Access to ServersПодробнее
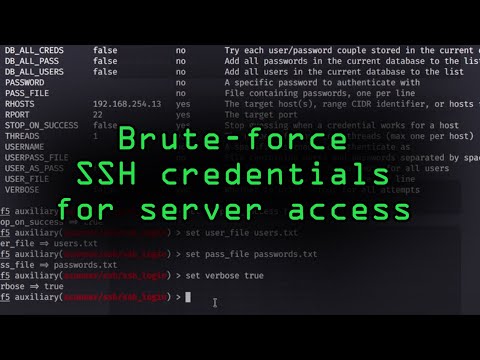
Jose Manuel Ortega - Ethical hacking with Python toolsПодробнее
