Exploiting Insecure Deserialization: Node-Serialize

CTF 4 Solution Writeup - Insecure Deserialization ClipПодробнее

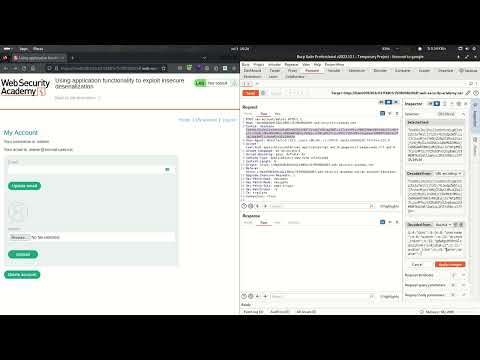
18.3 Using application functionality to exploit insecure deserializationПодробнее
Insecure Deserialization ExploitПодробнее

Privilege Escalation via Insecure DeserializationПодробнее

Exploit Java Deserialization | Discovering Insecure DeserializationПодробнее
Insecure Deserialization Attack ExplainedПодробнее

serialize to js exploit demoПодробнее

Insecure Deserialization | Applied Review #20Подробнее

Web Security Academy | Insecure Deserialization | 3 - Using Application Functionality To ExploitПодробнее

JBoss Insecure Deserialization ExploitПодробнее

Insecure Deserialization : Modifying serialized objects Portswigger LabПодробнее

Insecure Deserialization DemoПодробнее

Node.Js Deserialization AttackПодробнее

Exploiting Insecure Deserialization for Reverse ShellПодробнее

Understanding Insecure Deserialization Vulnerabilities: Security SimplifiedПодробнее

Insecure Deserialization | OWASPT Top 10Подробнее

Nodejs Exploitation: serializeПодробнее

DerpCon 2020 - .NET Roulette: Exploiting Insecure Deserialization in Telerik UI - Caleb GrossПодробнее
