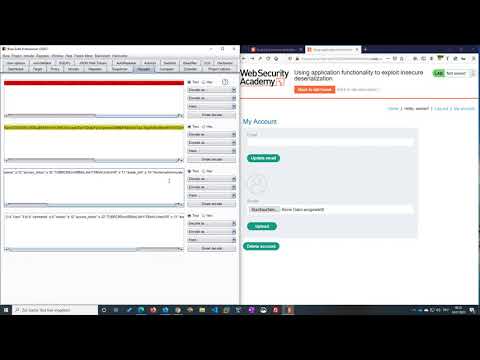
Web Security Academy | Insecure Deserialization | 3 - Using Application Functionality To Exploit

Web Security Academy | Insecure Deserialization | 8 - Developing A Custom Gadget Chain For Java DesПодробнее
Web Security Academy #083 Using application functionality to exploit insecure deserializationПодробнее

Web Security Academy | Insecure Deserialization | 6 - Exploiting PHP With A Pre-Built Gadget ChainПодробнее

Insecure Deserialization: Lab #7 - Exploiting Ruby deserialization using a documented gadget chainПодробнее
Insecure Deserialization:Lab #3- Using application functionality to exploit insecure deserializationПодробнее
Lab: Using application functionality to exploit insecure deserializationПодробнее

How to hack: USING APPLICATION FUNCTIONALITY TO EXPLOIT INSECURE DESERIALIZATION - Burp SuiteПодробнее

Lab Using application functionality to exploit insecure deserializationПодробнее

Burp Suite Certified Professional - Application Functionality to exploit Insecure DeserializationПодробнее

Using application functionality to exploit insecure deserializationПодробнее

Using application functionality to exploit insecure deserializationПодробнее
Using application functionality to exploit insecure deserialization (Video solution)Подробнее