Empire: Create Backdoor Undetected By All Anti-virus Using Kali Linux | Ethical Hacking #Hacking

How Hackers make Undetectable MalwareПодробнее

How to create fully undetectable payload using Kali Linux ? | Like a HackerПодробнее

Hacking Linux with These Simple Commands Pt:1Подробнее
This TOOL Makes You Disappear on KALI LINUX // FULL Beginner TUTORIALПодробнее

virus.pdfПодробнее

How Hackers Create Fully Undetectable Backdoors!Подробнее

How to Create Undetectable Payload backdoor In Urdu Hindi | Bypass All AntivirusПодробнее

Remotely Control Any PC in 4 mins 59 secondsПодробнее

HACKERLOI.pdfПодробнее

SQL Injection 101: Exploiting VulnerabilitiesПодробнее

Ethical Hacking Guide for Beginners | Learn Ethical Hacking #ytshortsindia #ethicalhacking #shortsПодробнее
Install a Backdoor: Step-by-Step Ethical Hacking Tutorial – Lec 62Подробнее

Using Crypter to Keep Malware Undetected by Antivirus | How Hackers create undetectable backdoorsПодробнее

Hacking into Android in 32 seconds | HID attack | Metasploit | PIN brute force PoCПодробнее

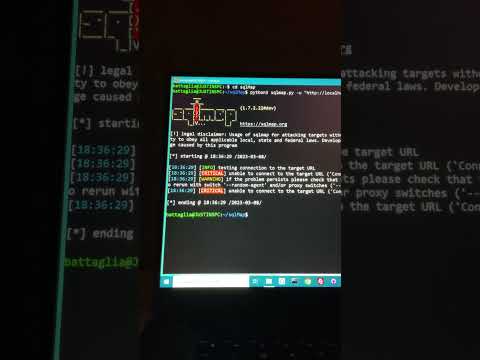
Hacking into the Bank with SQL MapПодробнее