How Hackers make Undetectable Malware

Uncover Exploits with XploitSniffer #XploitSniffer #AppSecurity #EthicalHackingПодробнее

How to create fully undetectable payload Using Metasploit | Ethical Hacking in Hindi.Подробнее

Setting up an UNDETECTABLE VM for Malware AnalysisПодробнее

How hackers hack with an image Trojan?!Подробнее
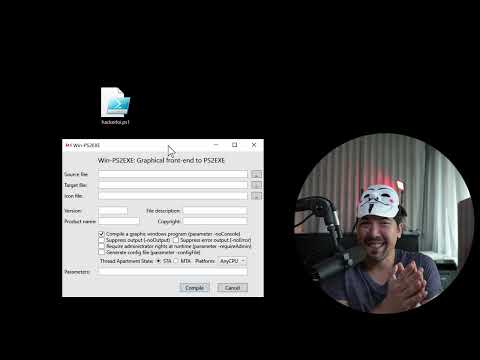
The Shocking Truth About Undetectable Malware and How to Protect YourselfПодробнее

How you get hacked: Undetected MalwareПодробнее

Anti Reverse Engineering | How Hackers Make Malware Undetectable & Difficult to Analyze | TryHackMeПодробнее

Malware analysis - server Encryption Learn how malicious threat actors create undetectable virusesПодробнее

Malware beats Windows Defender: How you get hackedПодробнее

BatCloak Engine Uses Jlaive File Builder to Create Undetectable MalwareПодробнее

How Hackers Write Malware & Evade Antivirus (Nim)Подробнее

How Hackers Make Undetectable Malware and Viruses!Подробнее
Undetectable malware for androidПодробнее

How Hackers Create Undetectable Malware and Viruses ll Dive into the Hacker's Toolkit 🛠️🔒Подробнее

Create Undetectable payloads using Villain- WindowsПодробнее

BatCloak Engine Uses Jlaive File Builder to Create Undetectable MalwareПодробнее

virus.pdfПодробнее

PDF PayloadПодробнее

How Hackers Create Undetectable Malware and VirusesПодробнее
