Exploiting PHP Object Deserialization | How To Be Bug Bounty Hunter
Understanding Insecure Deserialization Vulnerabilities: Security SimplifiedПодробнее

OWASP insecure deserialization explained with examplesПодробнее
Bug Bounty Hunting - PHP Code InjectionПодробнее

Intro to PHP Deserialization / Object InjectionПодробнее

PHP Object Injection & Serialization: Python Web Hacking | Natas: OverTheWire (Level 26)Подробнее

PHP Code Injection | Step By Step Guide | Bug Bounty Hunting |InfosecTrainПодробнее

Bug Bounty Bits: PHP code injectionПодробнее

Remote Code Execution (RCE) Vulnerability | FirstBlood v2 | Bug Bounty ServiceПодробнее
How to Exploit PHAR DeserializationПодробнее

Insecure Deserialization Attack ExplainedПодробнее

Approach to find Insecure deserialization | Exploitation | #cyberUFПодробнее

Insecure Deserialization:Lab #4 - Arbitrary object injection in PHPПодробнее
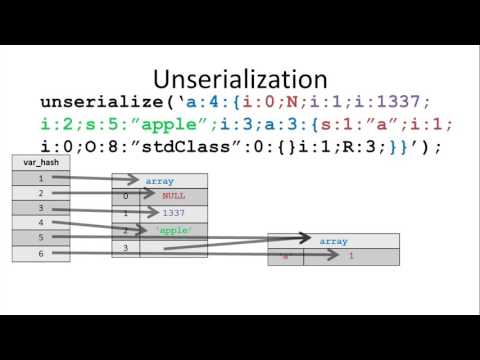
Exploiting PHP7 unserialize (33c3)Подробнее
xmlrpc.php vulnerability || Bug bounty pocПодробнее