Web Applications Vulnerabilities | Web Application Attack | Live Demo | Penetration Testing Tutorial

Live offensive penetration testing | Live VAPT by cyberbugs | In EnglishПодробнее

Complete Zap Tutorial: How to Use OWASP ZAP for Web Application Security TestingПодробнее

Live Hacking Tutorial: How to Think Like a Bug Bounty HunterПодробнее

LIve Bug Bounty Hunting | Unauthenticated Testing on Front.comПодробнее

Web Application Penetration Testing Tutorial Penetration Testing Tools #cybersecuritytrainingПодробнее
SQLMAP Tutorial in Hindi | How to find SQL injection in any website | CEH ToolПодробнее
Practical Bug BountyПодробнее

[Hindi] SQL Injection Attack Explained | Practical Demo | SQLiПодробнее
![[Hindi] SQL Injection Attack Explained | Practical Demo | SQLi](https://img.youtube.com/vi/lwqACxcFOO0/0.jpg)
Burp Clickbandit: How to perform clickjacking attack // Live HackingПодробнее

🔴 LIVE DEMO | How to Automate Vulnerability Scans? | #DevSecOps LIVEПодробнее

Basics of Burp(ing) for Testing Web App Security | Chris TraynorПодробнее

Cyber Security Full Course 2024 | Cyber Security Course Training For Beginners 2024 | SimplilearnПодробнее

Broken Access Control Vulnerabilities | FirstBlood v1 | Bug Bounty ServiceПодробнее
DEF CON 31 - The Art of Compromising C2 Servers A Web App Vulns Perspective - Vangelis StykasПодробнее
Testing for SQL injection vulnerabilities with Burp SuiteПодробнее
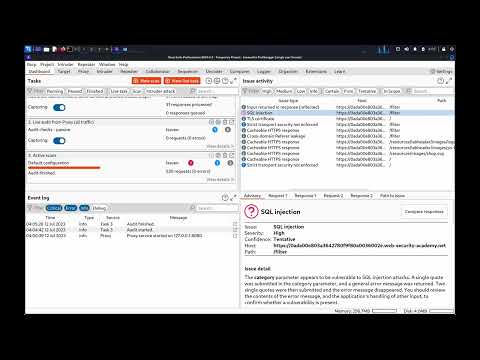
#HITB2022SIN #COMMSEC Exploiting Race Condition Vulnerabilities In Web Applications - Javan RasokatПодробнее

API Hacking Demo | Bug Bounty Web App TestingПодробнее
Cross Origin Resource Sharing (CORS) Vulnerability | BugBountyTraining | Bug Bounty ServiceПодробнее

Hacking Web Applications (2+ hours of content)Подробнее
