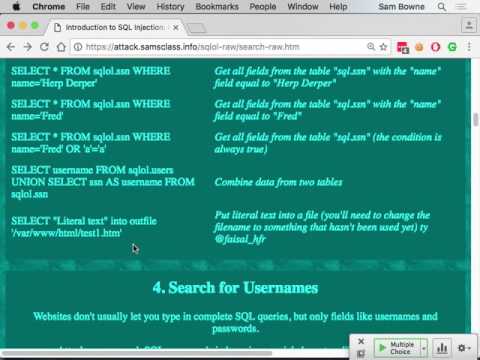
SQL Injection Attack: Find the Number of Columns in a Table | Ethical Hacking Tutorial
SQL Injection Attack Determine the number of columns | UNION AttackПодробнее
WTF is... SQL Injection (Part 2 - UNION Attacks)Подробнее

UNION attack, determining the number of columns returned by the query - Tamil | Web Academy SQLi LabПодробнее

SQL Injection Attack: Determine the number of columnsПодробнее
Create BACKDOOR with SQLMap! | Find any SQL Injection | SQLMap TutorialПодробнее

Lab: SQL injection UNION attack, finding a column containing text | In English |#sqli #sqlinjectionПодробнее
SQL for Hackers: Learn SQL Injection and Database Security for Penetration TestingПодробнее
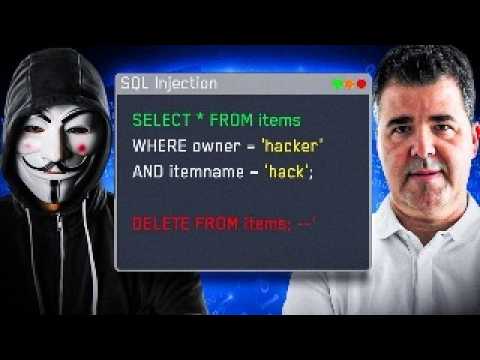
SQL Injection Attack Cyber Security CourseПодробнее

SQL Injection UNION Attack, Determining The Number Of Columns Returned By The Query | Lab SolvedПодробнее

Easy Ethical Hacking: SQL Injection with Burp Suite using Union StatementsПодробнее
Exploiting SQL Injection Vulnerability ManuallyПодробнее
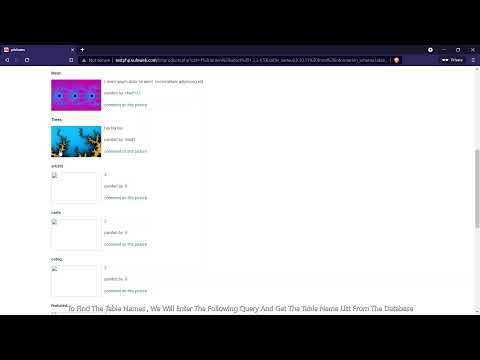
sql injection union attack finding a column containing text | Burpsuite portswigger labПодробнее
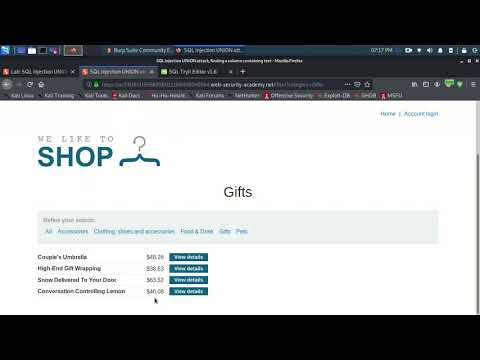
CNIT 129S: 9: Attacking Data Stores (Part 1 of 3)Подробнее