Simplified DES(Data Encryption Standard)(Information Security)
The Data Encryption Standard DESПодробнее

Simplified DES (Data Encryption Standard) | Practical Example | Lecture 5Подробнее

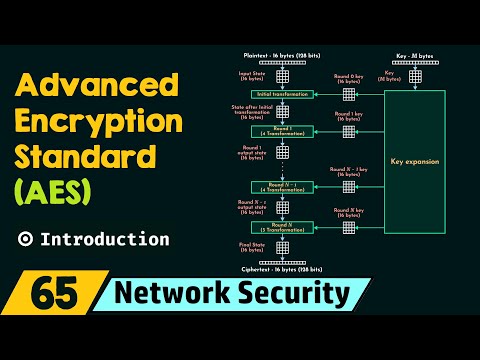
Introduction to Advanced Encryption Standard (AES)Подробнее
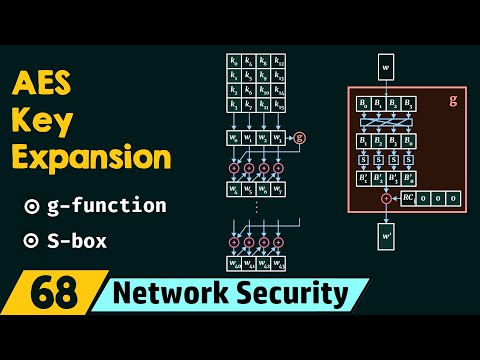
AES Key ExpansionПодробнее
Simplified DES in Tamil (SDES Algorithm in Tamil ) | Example sum | problem solved | Network securityПодробнее

Python implementation of Simplified Data Encryption Standard (S-DES)Подробнее

2.14 DES Algorithm in TamilПодробнее

DES Algorithm in cryptography & network security explain in Telugu #DES Algorithm #telugu#cryptograПодробнее

Data Encryption Standard (DES) - Solved QuestionsПодробнее

Avalanche Effect and the Strength of DESПодробнее

Data Encryption Standard [DES] Algorithm - [PART-2]Подробнее
![Data Encryption Standard [DES] Algorithm - [PART-2]](https://img.youtube.com/vi/O1TmUyrWn4g/0.jpg)
Cryptography Simple DES encryption with exampleПодробнее

Simplified Advanced Encryption Standard (S-AES) | JUST UniversityПодробнее

Cyber Security L 10 | DES| S-box| P- box| XOR & Swap |Btechcse | kuk uniПодробнее

Key Scheduling and Decryption in DESПодробнее

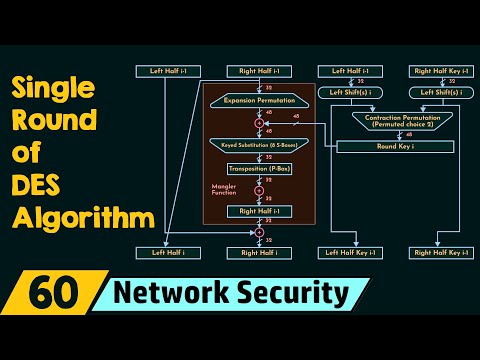
Single Round of DES AlgorithmПодробнее
Data Encryption StandardПодробнее

S-DES Algorithm | Generating K1 and K2 from Key | Information SecurityПодробнее

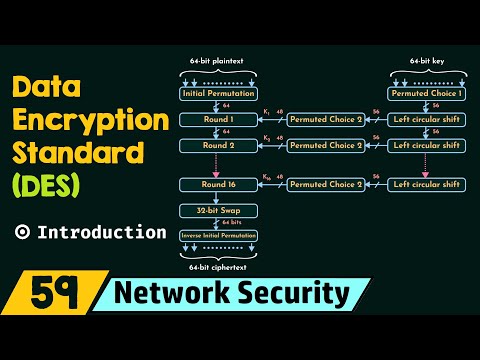
Introduction to Data Encryption Standard (DES)Подробнее
The F Function of DES (Mangler Function)Подробнее
