SHA-512 ALGORITHM || SECURE HASH ALGORITHM || CRYPTOGRAPHIC HASH FUNCTIONS || NETWORK SECURITY
SHA-256 & SHA-512 Explained 🔥 | Secure Hashing Algorithm TutorialПодробнее

hash function salt decrypter unhash password onlineПодробнее

hashing in python using hashlib library for secure hashingПодробнее
Implementing SHA-512 Password Hashing in C#Подробнее

Is SHA 512 Secure? - SecurityFirstCorp.comПодробнее

Secure Hash Algorithm (SHA) in Cryptography and Network Security #cryptography #networking #securityПодробнее
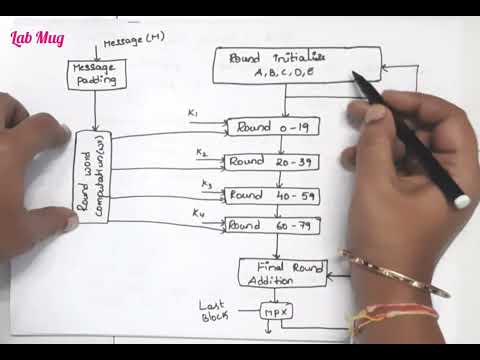
Is SHA512 Secure? - SecurityFirstCorp.comПодробнее

Netsec Crypto Hash 6 - Some Secure Hash AlgorithmsПодробнее
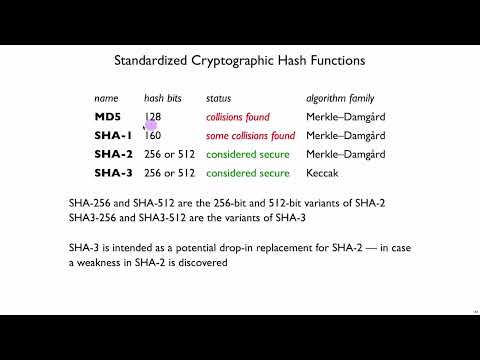
CNS Subject Complete Unit 3 Topics | Cryptography and Network Security #conceptclearbydrmvk #jntuhПодробнее

** Master Hashing: MD5 ,Blake2 to SHA512!**Подробнее

Hashing and Hashing Algorithms - md5 sha1 sha256 sha2 sha3 - Cryptography EssentialsПодробнее
Cryptographic Hash Function (CHF) in Cryptography || Network Security in TeluguПодробнее

java sha512 exampleПодробнее

Hash functions // Network SecurityПодробнее

SHA Algorithm Explained | Unit 4 Cryptography and Cyber Security (CB3491) | Anna UniversityПодробнее

#Authentication Requirements In Cryptography and Network Security #cns #jntuh #conceptclearbydrmvkПодробнее

SHA function in Cryptography and cyber security tamil||CCS||Anna university reg-2021.Подробнее

Introduction to Secure Hash Algorithm SHA 512 || Lesson 74 || Cryptography ||Подробнее

#SHA Secure Hash Algorithm #sha512 Algorithm with example #CNS #jntuh #feed #conceptclearbydrmvkПодробнее

hashing in python using hashlib library for secure hashingПодробнее