picoCTF 2022 | Reverse Engineering | unpackme

Tutorial PicoCTF 2022 (98): Reverse Engineering: patchme.py, Safe Opener, unpackme.pyПодробнее

Unpacking Linux Binaries | picoCTF 2022 #07 "unpackme"Подробнее

picoCTF 2022 - Reverse Engineering (Part 3)Подробнее

picoCTF unpackme-py walkthrough - Reverse EngineeringПодробнее

Reverse Engineering: picoCTF Unpackme upx challengeПодробнее

Unpacking UPX Binaries (PicoCTF 2022 #51 'unpackme')Подробнее

Decrypting Packed Python Code (PicoCTF 2022 #28 'unpackme.py')Подробнее
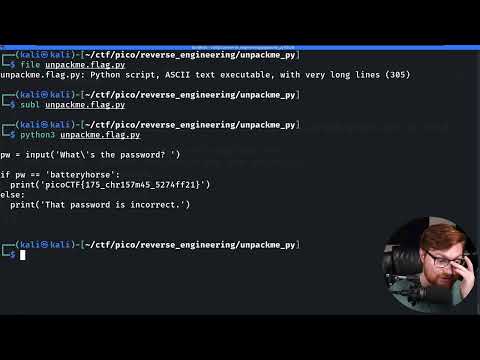
picoGym (picoCTF) Exercise: unpackme.pyПодробнее

picoCTF 2022 | Reverse Engineering | unpackme.pyПодробнее

picoGym (picoCTF) Exercise: unpackmeПодробнее

Reverse Engineering (RE) Challenge Walkthroughs - PicoCTF 2022 (BEGINNER-FRIENDLY Capture The Flag)Подробнее

unpackme | Reverse Engineering Binary | PicoCTF 2022Подробнее

pico2022 unpackme.pyПодробнее
