Missing Functional Level Access Control (A5 of the OWASP Top 10) - Secure Code Warrior Explainer
What is Missing Function Level Access Control? | OWASP Top 10 2013 | Video by DetectifyПодробнее

OWASP TOP 10 A7- Missing Function Level Access ControlПодробнее

OS Command Injections | Owasp Top 10 Explainer Video | Secure Code WarriorПодробнее

OWASP Top 10 Vulnerabilities #7 Missing Function Level Access ControlПодробнее

OWASP Top 10 - A7 Missing function-level access controlПодробнее

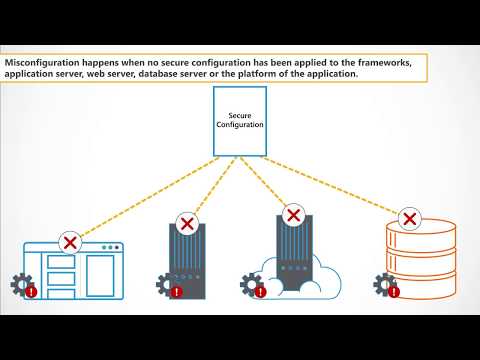
Security Misconfiguration | Owasp Top 10 Explainer Video | Secure Code WarriorПодробнее
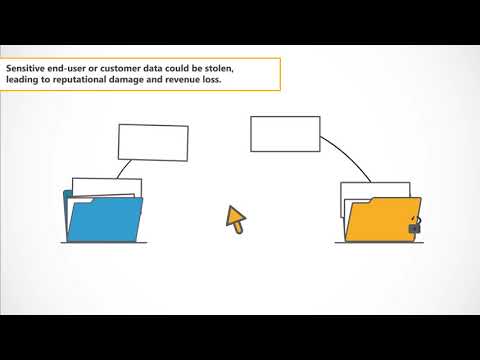
Coders Conquer Security OWASP Top 10 API Series: Missing Object Level Access ControlПодробнее

Professionally Evil Fundamentals: OWASP Top 10 A5 Broken Access ControlПодробнее

Server-Side Request Forgery: Hacking the OWASP Top 10Подробнее
Coders Conquer Security OWASP Top 10 API Series: Insufficient Logging and MonitoringПодробнее

Missing Function Level Access Control ExploitsПодробнее

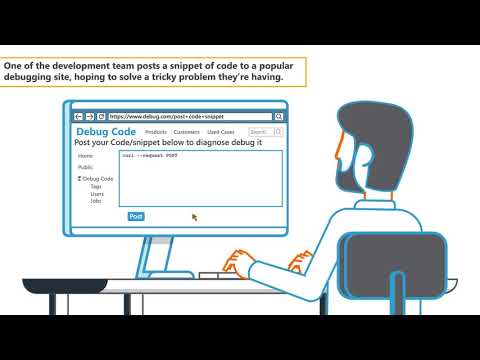
Coders Conquer Security OWASP Top 10 API Series: Security Misconfiguration (Debug Features Enabled)Подробнее

Part two -Missing Function Level Access ControlПодробнее

LDAP Injections | Owasp Top 10 Explainer Video | Secure Code WarriorПодробнее

OWASP Top 10 2017 | A5: Broken Access ControlПодробнее

Missing Function Level Access Control DefenseПодробнее

Insufficient Transport Layer Protection | Owasp Top 10 Explainer Video | Secure Code WarriorПодробнее
Coders Conquer Security OWASP Top 10 API Series: Improper Assets ManagementПодробнее