MAN IN THE MIDDLE ATTACK | MITM ATTACK EXPLAINED IN HINDI | HOW MITM ATTACK WORKS ?
How to Spy on Any Network using MITM Attacks in Kali Linux?Подробнее
Man-in-the-Middle Attacks with Ettercap! #MITM #CyberSecurity #NetworkHacking #EthicalHackingПодробнее

MITM Attack 🔥 Man In The Middlle Attack #mitm #hacking #shortsПодробнее

MITM Attack 🔥 Man In The Middle Attack | How it's works | Cyber Agent |Подробнее

Объяснение атаки спуфинга ArpПодробнее

Man In the Middle Attack | All Tools ExplainedПодробнее

MITM Attack Explained In Hindi - Tutorial For BeginnersПодробнее

[Hindi] Man in the Middle Attack in Hindi | How MITM attack worksПодробнее
![[Hindi] Man in the Middle Attack in Hindi | How MITM attack works](https://img.youtube.com/vi/Bt43RUxunuA/0.jpg)
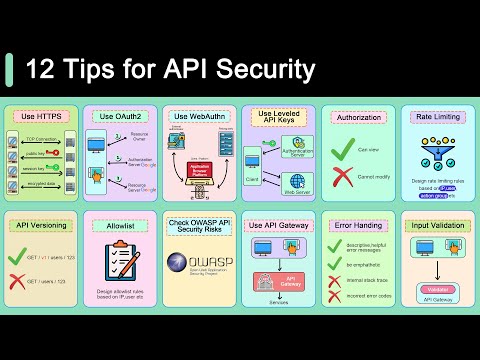
Top 12 Tips For API SecurityПодробнее
Cybersecurity क्या है? | What Is Cybersecurity [Hindi]| Cyber Security Explained HINDI | SimplilearnПодробнее
![Cybersecurity क्या है? | What Is Cybersecurity [Hindi]| Cyber Security Explained HINDI | Simplilearn](https://img.youtube.com/vi/iGqQahWV-xA/0.jpg)
What is a Man-in-the-Middle Attack? How to Protect Yourself (Before it's Too Late)Подробнее

Man-in-the-Middle Attack _ ARP Poisoning/Spoofing using EttercapПодробнее

BEWARE! Hackers Can Capture Your Internet Traffic - Man In The Middle Attack Explained In Bangla!Подробнее

#22 - Man In The Middle Attack (MitM) |Cyber Security Tutorial @CodingStuntsOfficialПодробнее

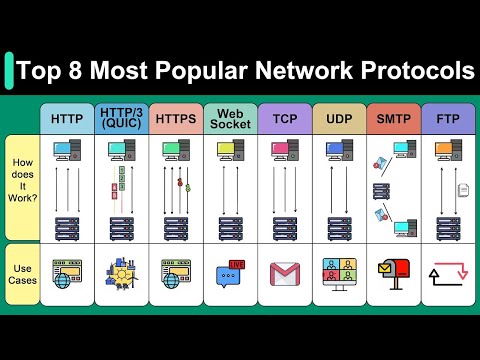
Top 8 Most Popular Network Protocols ExplainedПодробнее
Pwnagotchi — hacking WiFi networks in seconds | Real ExperimentПодробнее
Man in the Browser (MITB) Attack Explained: Working and Security MeasuresПодробнее

What is a Man in the Middle MitM Attack?Подробнее

WiFi Pineapple | WiFi Hacking Gadget Available on Amazon | By Technical UstadjiПодробнее
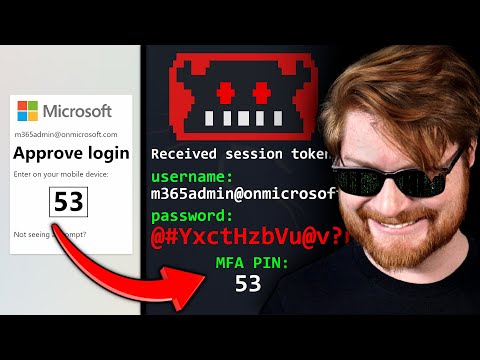
I Stole a Microsoft 365 Account. Here's How.Подробнее