Kerberos Attacks Explained | Windows Active Directory Attacks

⚠️ Don't Get Roasted! Understanding Kerberoasting Attacks on Your SystemПодробнее
Hacking Active Directory for Beginners (over 5 hours of content!)Подробнее

Domain Admin: Bloodhound, Mimikatz, Pass-The-Hash & Golden ticket.Подробнее
Attacking active directory | kerberoastingПодробнее

Kerberoasting Attack: Active Directory Penetration Testing #cybersecurity #shortsПодробнее

Learn Active Directory KerberoastingПодробнее
Active Directory Lab: Set Up and Test ASREPRoast and Kerberoasting Attacks Part 1Подробнее

attacking Active Directory | GOLDEN TICKETПодробнее

attacking active directory | DCSYNC attackПодробнее
Attack Tutorial: How a Pass the Hash Attack WorksПодробнее

Threat Research - Active Directory Kerberos AttacksПодробнее

Active Directory Attacks : AS-REP RoastingПодробнее
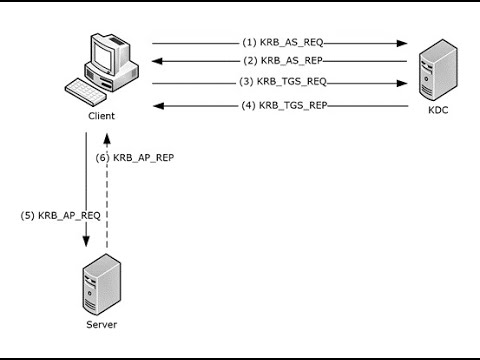
Attacking Active Directory: Unleashing the Power of Unconstrained DelegationПодробнее
attack active directory for beginners with hackthebox | kerberos hackingПодробнее

Kerberos vs. LDAP: What’s the Difference?Подробнее
Attack Tutorial: How Silver Ticket Attack WorksПодробнее

Attack Tutorial: How the Kerberoasting Attack WorksПодробнее

Active Directory - Demo of Unconstrained Delegation AttackПодробнее
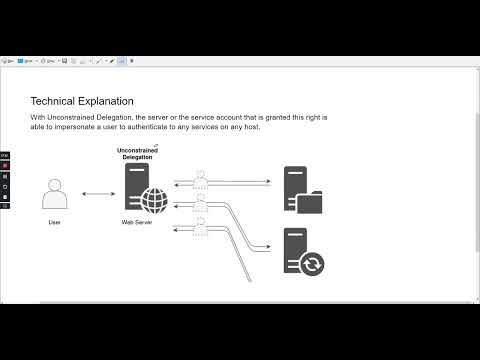
Breaking Kerberos' RC4 Cipher and Spoofing Windows PACsПодробнее
