k-anonymity explained

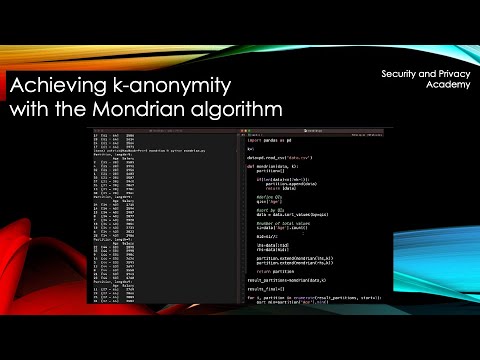
Step-by-Step implementation of k-anonymity with the Mondrian Algorithm in PythonПодробнее
Differential Privacy explainedПодробнее

t-closeness explainedПодробнее

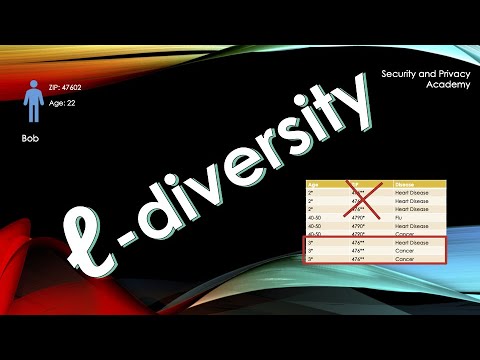
L-Diversity explainedПодробнее
K-Anonymization Part 2 #privatemeasurement #kanonymity #dataanalysis #digitalmarketing #measurementПодробнее

Anonymization techniques and Differential PrivacyПодробнее

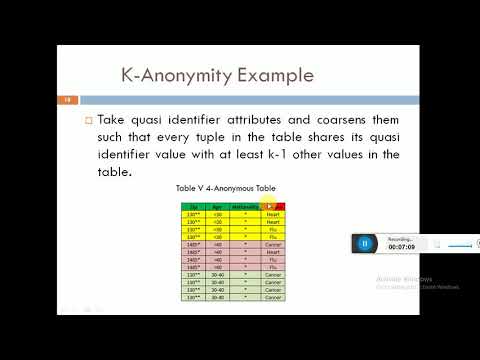
k anonymityПодробнее

Lecture 1B: Some Attempts at Data Privacy - Neural Networks, Medical Studies, k-AnonymityПодробнее

What is Anonymity | Explained in Tamil | Dilshan DigitalsПодробнее

Linking Attack and K-AnonymityПодробнее
K-Anonymization or why Aggregation is not EnoughПодробнее

Scaling Postgres Episode 89 Performance Impressions | Mystery Solving | GiST Indexes | K-AnonymityПодробнее

The Caching Secrets of Pwned PasswordsПодробнее

Protecting Sensitive Data in Huge Datasets (Cloud Next '19)Подробнее

Internet of Things: k-anonymityПодробнее

Eva Infeld - Matching Theory and Anonymity [11 Mar 2016]Подробнее
![Eva Infeld - Matching Theory and Anonymity [11 Mar 2016]](https://img.youtube.com/vi/keqWXeYo5sg/0.jpg)
Privacy and k Anonymity anonymityПодробнее

Crowd-Blending PrivacyПодробнее

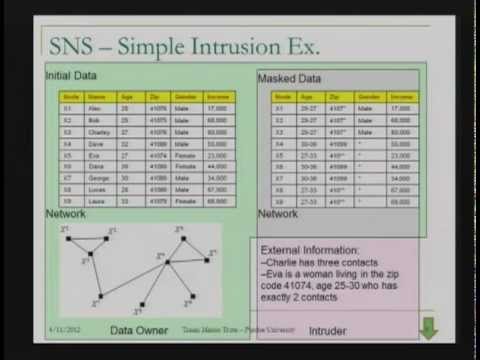
2012-04-11 - : K-Anonymity in Social Networks: A Clustering Approach - CERIAS Security SeminarПодробнее