Java exploiting with ysoserial and how gadget chains work
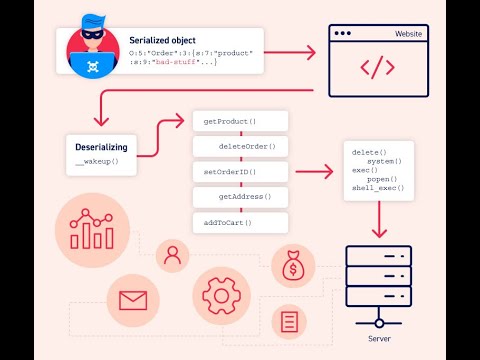
Insecure Deserialization: Lab #8: Developing a custom gadget chain for Java deserializationПодробнее
Exploiting Java deserialization with Apache CommonsПодробнее
All-Army Cyberstakes! Ysoserial EXPLOIT - Java DeserializationПодробнее

Automated Discovery of Deserialization Gadget ChainsПодробнее

Automated Discovery of Deserialization Gadget ChainsПодробнее

Deserialization Vulnerability Remediation with Automated Gadget Chain Discovery - Ian HakenПодробнее

Preventing Deserialization attacks in Java applicationsПодробнее

LookingSerial - adjusting my script for automating ysoserial for specific caseПодробнее
Exploit Java Deserialization | Exploiting JBoss 6.1.0Подробнее
Pwning Your Java Messaging With Deserialization VulnerabilitiesПодробнее
Deserialization All-In-OneПодробнее
Developing a custom gadget chain for Java deserialization (Video solution)Подробнее
Lab: Exploiting Java deserialization with Apache CommonsПодробнее
Exploit Java Deserialization | Discovering Insecure DeserializationПодробнее
Developing a custom gadget chain for Java deserializationПодробнее
Black Hat USA 2018 - Automated Discovery of Deserialization Gadget ChainsПодробнее

Insecure Deserialization: Lab #7 - Exploiting Ruby deserialization using a documented gadget chainПодробнее
J-Fall 2021: Brian Vermeer - Deserialization exploits in Java: why should I care?Подробнее

Web Security Academy | Insecure Deserialization | 5 - Exploiting Java Deserialization Apache CommonsПодробнее