Is your MikroTik vulnerable...?

Ultimate MikroTik Network Segmentation Guide for CybersecurityПодробнее

Vulnerability Attack in MikroTik Python ExploitПодробнее

Critical Vulnerability in MikroTik RouterOS Exposes 500,000+ Devices to Privilege EscalationПодробнее

~1m MikroTik routers vulnerable 💻Подробнее

Almost 1 Million Routers Vulnerable to Hijacking | MikroTik RouterOS HackПодробнее

A Deep Dive into Overlooked MikroTik Pre-Authentication Vulnerabilities | TechAcdntПодробнее

DEF CON 31 - Review on the Less Traveled Road - 9 Yrs of Overlooked MikroTik PreAuth RCE - NiNi ChenПодробнее

Critical Vulnerability in MikroTik RouterOS Exposes 500,000+ Devices to Privilege EscalationПодробнее

900,000 MikroTik Routers At Risk | cybernews.comПодробнее

Security analysis of recent RouterOS exploitsПодробнее

11/1/19 MikroTik Router Vulnerabilities Grant Backdoor Access | AT&T ThreatTraqПодробнее

Jacob Baines - Help Me Vulnerabilities You're My Only Hope - DEF CON 27 ConferenceПодробнее

DEF CON 27 - Jacob Baines - Help Me Vulnerabilities Youre My Only HopeПодробнее

Router Hacking Made Easy with RouterSploit: Unlocking Router VulnerabilitiesПодробнее

How I caught #hackers with #mikrotik!!!!! 🕵🏾♂️Подробнее

TheBrothersWISP 86 - Mikrotik IPv6 Vulnerability, MTK Indoor, Technology's ImpactПодробнее

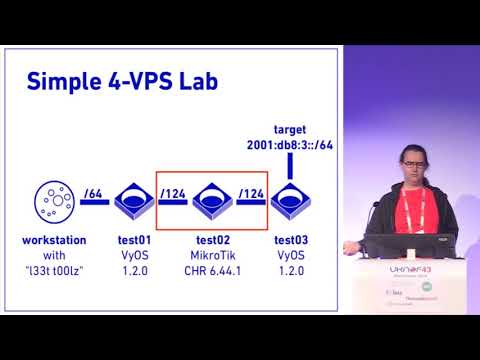
UKNOF43 - Scanning IPv6 Address Space… and the remote vulnerabilities it uncoversПодробнее
Is your Router Hackable ? (Gaining Access To Routers)Подробнее
Oeliander | MikroTik Vulnerability Assessment ToolПодробнее
