Introduction to JWT Attacks

Understanding JWT Attacks Part 4 : Token with No Signature | JWT Attacks Series | Hindi TutorialПодробнее

Understanding JWT Attacks Part 3: Practical Demonstration | JWT Attacks Series | Hindi TutorialПодробнее

JWT Authentication Bypass via jku Header InjectionПодробнее
JWT Authentication Bypass via kid Header Path TraversalПодробнее

JWT Authentication Bypass via Flawed Signature VerificationПодробнее
Introduction to JWT Tokens || JWT Attacks || All About JWT || Hindi Tutorial || part 1Подробнее

JWT Authentication Bypass via Algorithm ConfusionПодробнее
JWT Authentication Bypass via Algorithm Confusion with No Exposed KeyПодробнее
JWT Authentication Bypass via jwk Header InjectionПодробнее
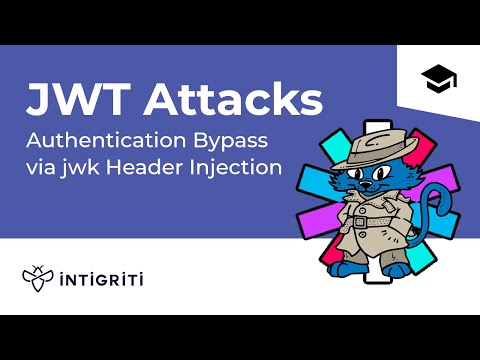
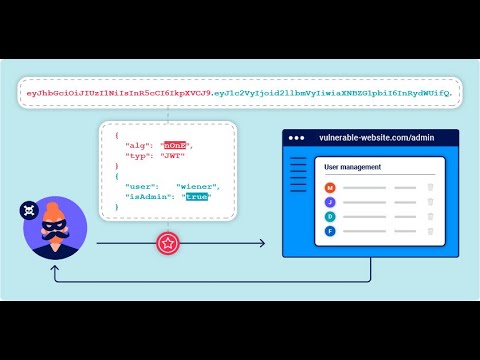
JWT Authentication Bypass via Unverified SignatureПодробнее

JWT Attacks #1 - JWT authentication bypass via unverified signatureПодробнее

JWT Attacks #5 - JWT authentication bypass via jku header injectionПодробнее

JWT Attacks #7 - JWT authentication bypass via algorithm confusionПодробнее
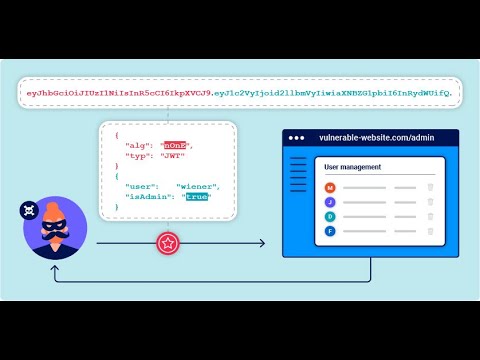
JWT Attacks #8 - JWT authentication bypass via algorithm confusion with no exposed keyПодробнее
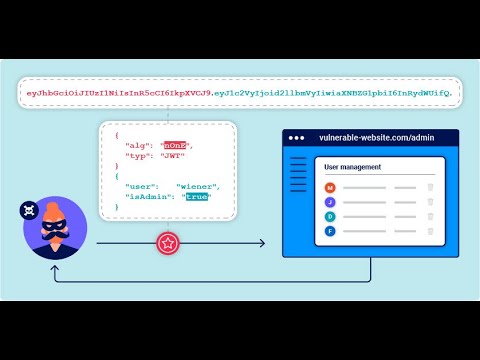
JSON Web tokens attacks (JWT) part 2 شرح ثغرهПодробнее

JWT Attacks #3 - JWT authentication bypass via weak signing keyПодробнее
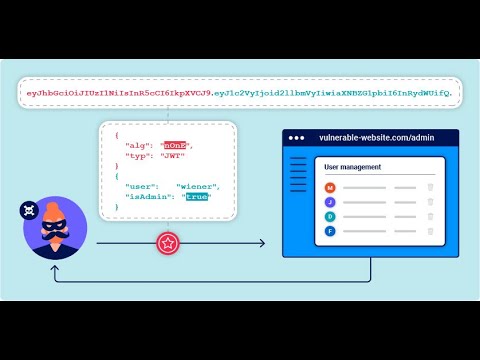
JWT Attacks #4 - JWT authentication bypass via jwk header injectionПодробнее
JSON Web tokens attacks (JWT) part 1 شرح ثغرهПодробнее

Attacking JWT - Header InjectionsПодробнее
