Implementing Endpoint Privilege Management in Microsoft 365
MD-102: Explore Microsoft Intune SuiteПодробнее

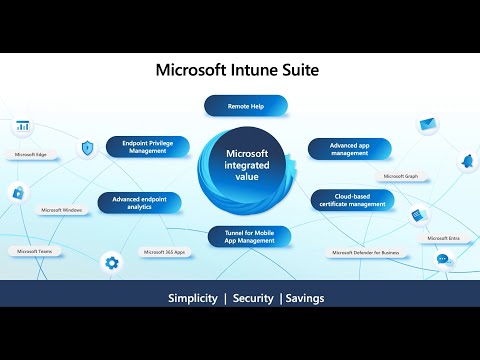
Microsoft Intune Suite The Essential Beginners GuideПодробнее

Microsoft Endpoint Privilege ManagementПодробнее

What's new in Microsoft Intune (2309)Подробнее

M365UK Jun 2024 Information Compliance and Endpoint Privilege ManagementПодробнее

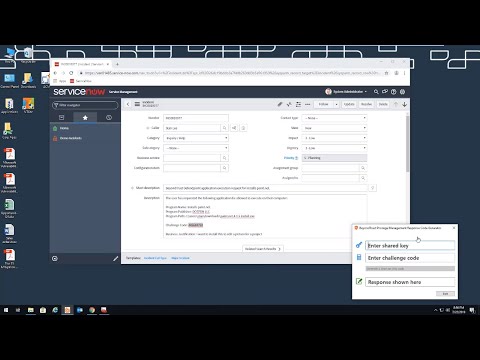
How to Configure Support Approved EPM Elevation using Intune | Highly secured optionПодробнее

Microsoft Intune reinvents Mac managementПодробнее

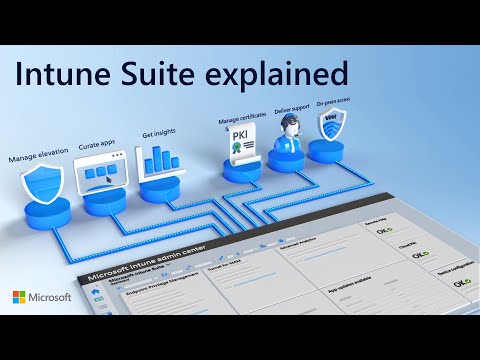
Microsoft Intune Suite - beyond endpoint management in 2024Подробнее
How BeyondTrust Privilege Management for Windows and Mac WorksПодробнее
Microsoft Intune Suite - Endpoint Privilege Management Elevation RulesПодробнее

Security best practices for managing across platforms with Endpoint ManagerПодробнее

Endpoint Privilege Management (EPM) – Intune Windows Basics 20Подробнее
What's new in Microsoft Intune (2304)Подробнее
Intune Endpoint Privilege ManagementПодробнее
S04E12 - Microsoft Intune Suite - Endpoint Privilege Management with Special Host Matt Call (I.T)Подробнее
Limit your attack surface with Endpoint Privilege Management - Microsoft Tech AcceleratorПодробнее