How to Intercept Traffic Using Mitmproxy | Hack Earth #hack #cybersecurity #ethicalhacking #hacker

how Hackers SNiFF (capture) network traffic // MiTM attackПодробнее

Ethical Hacking Guide for Beginners | Learn Ethical Hacking #ytshortsindia #ethicalhacking #shortsПодробнее
Intercepting Communications of IoT Device with ARP Poisoning and MITMProxyПодробнее

Apple Will Pay Hackers $1,000,000 For This Bug Bounty 😳Подробнее

Hacking KnowledgeПодробнее

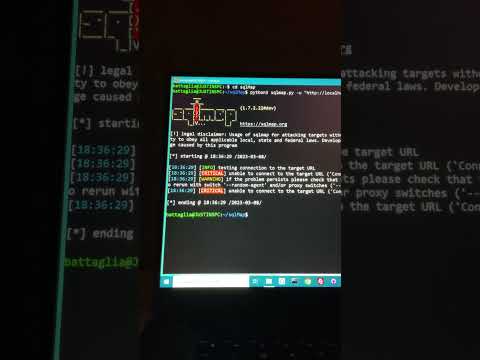
Hacking into the Bank with SQL MapПодробнее
How hackers brute force FTP service #cybersecurity #hacking #cyber #security #hacktheplanetПодробнее

Capture, Analyze and Debug HTTPS traffic with MITMProxyПодробнее

🔥 Capturing HTTPS Traffic and Viewing it in PLAIN TEXT with MITMProxy 🔥Подробнее

Bug Bounty expectations vs Reality 😂🔥Подробнее
Configuring Traffic Blocklisting with Google Cloud Armor | #qwiklabs #coursera [With Explanation🗣️]Подробнее
![Configuring Traffic Blocklisting with Google Cloud Armor | #qwiklabs #coursera [With Explanation🗣️]](https://img.youtube.com/vi/wEpq-gozPZc/0.jpg)
Get Proxy - Metasploit Minute [Cyber Security Education]Подробнее
![Get Proxy - Metasploit Minute [Cyber Security Education]](https://img.youtube.com/vi/7WsR3vyZKQo/0.jpg)
SQL Injection 101: Exploiting VulnerabilitiesПодробнее

Found Bug in Canon 📸 | Live Bug Hunting #cybersecurity #ethicalhacking #bugbountyПодробнее

Hacking into Android in 32 seconds | HID attack | Metasploit | PIN brute force PoCПодробнее

Hacking 🔥 Expectation vs Reality | Coding Status For WhatsAppПодробнее

How Hackers SNiFF (capture) Network Traffic | MiTM Attack & how to secureПодробнее

Bug Bounty is Just Unpaid PentestsПодробнее
