How to Detect and Prevent Log4Shell with VMware vDefend ATP

How to Mitigate Multi-stage Ransomware Attacks Using VMware vDefend ATPПодробнее

Understanding the Log4j Vulnerability | Exploiting VMware VCenter & a reverse shell🔥| Patch NOW!Подробнее

Log4Shell ExplainedПодробнее

CVE-2021-44228 (Log4Shell) - Exploitation/DetectionПодробнее
[EN] VMware: How to detect the Log4j vulnerability on vCenter with Runecast, and how to patch itПодробнее
![[EN] VMware: How to detect the Log4j vulnerability on vCenter with Runecast, and how to patch it](https://img.youtube.com/vi/i0Lpc5EGa-Q/0.jpg)
How to setup a Pentesting Lab on VMWare ?Подробнее

How to Deploy and Configure VMware vDefend IDS/IPSПодробнее

Fastest way to hunt for Log4shell CVE-2021-44228 log4j vulnerability exploitation and attacksПодробнее

Apache Log4j (Log4Shell) Vulnerability – DEMO How to discover, detect and protectПодробнее

Log4Shell Apache Vulnerability: What to Know and What to DoПодробнее

VMWare vCenter Log4J Workaround | VMSA-2021-0028 | CVE-2021-44228Подробнее

What is Log4Shell Vulnerability? Check 4-Step Immediate Mitigation for Log4j AttacksПодробнее
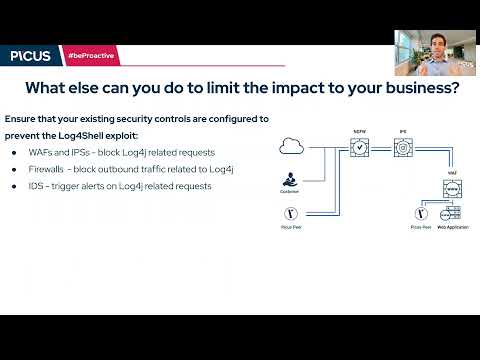
Log4J Vulnerability vmware vCenter Workaround (CVE-2021-44228)Подробнее

[Demo] Apache Log4j (Log4Shell) Vulnerability – How to use Cloud One to discover, detect and protectПодробнее
![[Demo] Apache Log4j (Log4Shell) Vulnerability – How to use Cloud One to discover, detect and protect](https://img.youtube.com/vi/CorEsXv3Trc/0.jpg)
Tutorial How To Access Tor Securely through Ubuntu VMПодробнее

Log4j VMWare VCenter ExploitПодробнее

VMware NSX-T 3.2 ATP and Ransomware investigationПодробнее

log4shell exploit demoПодробнее
