How to build a Zero Trust and Data Centric Network- Scenario introduction #cybersecurity

COMPLETE Cybersecurity RoadmapПодробнее
A Simplified and Practical Approach to Pursuing a Zero Trust ArchitectureПодробнее

How to Build a Zero Trust Network Part 1Подробнее

Zero Trust Overview (part 1)Подробнее

Zero Trust Explained in 4 minsПодробнее
A Data Centric Approach to Zero TrustПодробнее

Implementing a Zero Trust ArchitectureПодробнее

zerotrust networkПодробнее

Cybersecurity and Zero TrustПодробнее

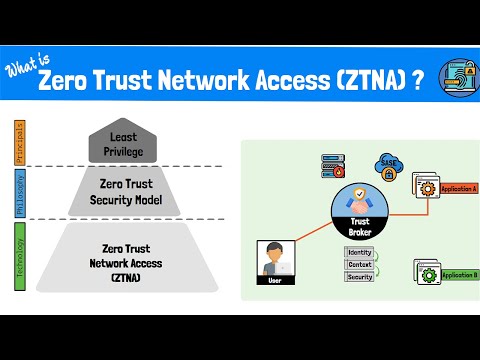
What is Zero Trust Network Access (ZTNA)? The Zero Trust Model, Framework and Technologies ExplainedПодробнее
Data Centric Zero Trust for a Remote First WorldПодробнее

Zero Trust approach with Data Centric Security - OpenTextПодробнее

Zero Trust - Course OverviewПодробнее

Why Data Centric Security is Essential for a Zero Trust FrameworkПодробнее

Create Data Centric Zero Trust Architecture with the NIST Cybersecurity Framework with RackTopПодробнее

Cybersecurity, Reimagined Part 2 | Zero Trust Explained & How to "Shift Up" Your Security Approach.Подробнее

Data centric approach to zero trustПодробнее

Dragos Webinar: Manageable Zero Trust for OT NetworksПодробнее

A Day in the Life of Cyber Security | SOC Analyst | Penetration Tester | Cyber Security TrainingПодробнее

How Zero Trust Security WorksПодробнее
