Hack with PHP, Web Shell con Weevely | Web Shell with Weevely Kali Linux 2021.2
How To Use Weevely PHP Backdoor --A HACK DAY--Подробнее
Generating A PHP Backdoor with weevelyПодробнее

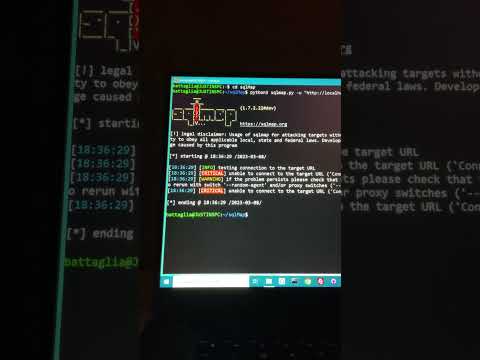
Hacking into the Bank with SQL MapПодробнее
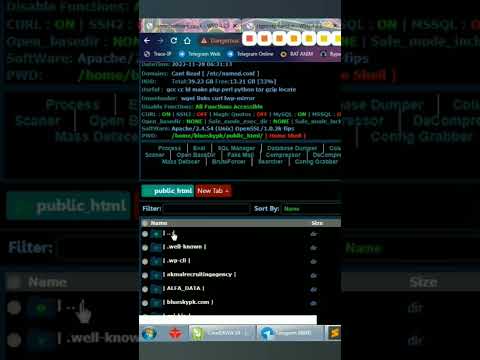
WEB SHELLПодробнее
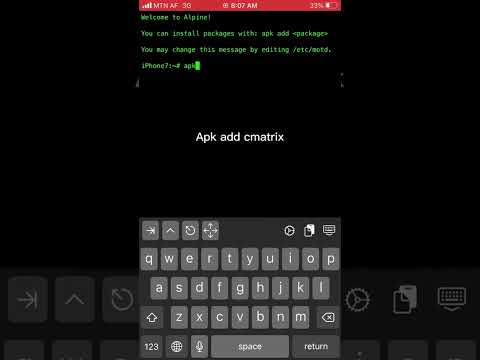
Ish shell full hackПодробнее
Weevely PHP Backdoor | Web Hacking For Beginners | 2022Подробнее
Hacking DV-Pi 3 using WeevelyПодробнее

Web Shell Uploading Techniques & Exploitation Using Kali Linux #bugbounty #hacking #hackersПодробнее
How to create a PHP web shell | bug bountyПодробнее
Top 5 Things to Know About Web ShellПодробнее
Ish shell hackПодробнее
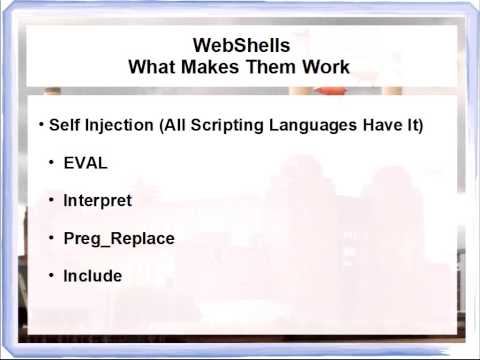
Anatomy of a WebShell - D0n Quix0teПодробнее
How to get stable reverse shell through PHP Pentest-Monkey with malicious file upload vulnerabilityПодробнее
[Upload shell PHP] Shell weevely3 by BinPCПодробнее
![[Upload shell PHP] Shell weevely3 by BinPC](https://img.youtube.com/vi/yha2sdbEhqg/0.jpg)
RFI com WebShell PHP e NetCatПодробнее

Kali Pen Test Lab - 5. Low Security Basic File Upload ExploitationПодробнее
Hacking Website Using PHP Shell/PHP BackdoorПодробнее

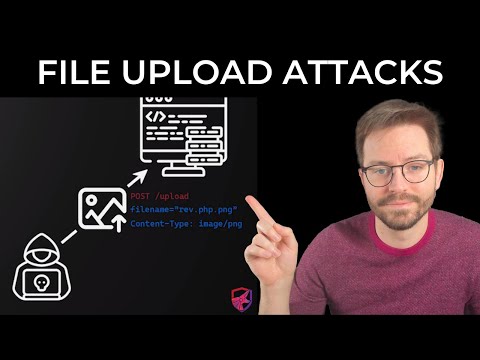
Web Application Hacking - File Upload Attacks ExplainedПодробнее
Binary Exploitation vs. Web SecurityПодробнее
