File Upload Vulnerability | FirstBlood v2 | Bug Bounty Service

Business Logic Vulnerability with hidden input | FirstBlood v3 | Bug Bounty ServiceПодробнее

Authentication Brute Force Vulnerability | FirstBlood v3| Bug Bounty ServiceПодробнее

Remote Code Execution (RCE) Vulnerability | FirstBlood v2 | Bug Bounty ServiceПодробнее
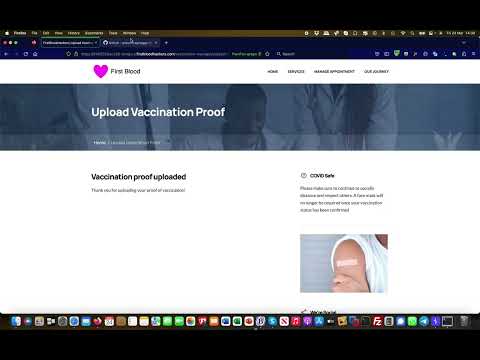
SQL Injection Vulnerability | FirstBlood v2 | Bug Bounty ServiceПодробнее
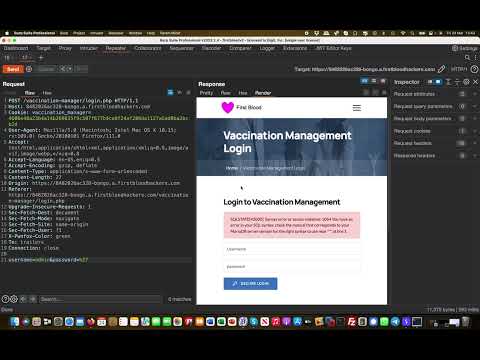
Account Takeover (ATO) Vulnerability | FirstBlood v2 | Bug Bounty ServiceПодробнее

Insecure Direct Object Reference (IDOR) Vulnerability | FirstBlood v2 | Bug Bounty ServiceПодробнее

Broken Access Control Vulnerabilities | FirstBlood v1 | Bug Bounty ServiceПодробнее
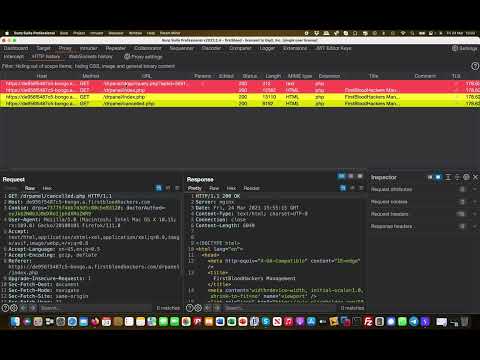
Application / Business Logic Vulnerability | FirstBlood v1 | Bug Bounty Service 5 business logicПодробнее

Information Disclosure Vulnerability | FirstBlood v1 | Bug Bounty ServiceПодробнее
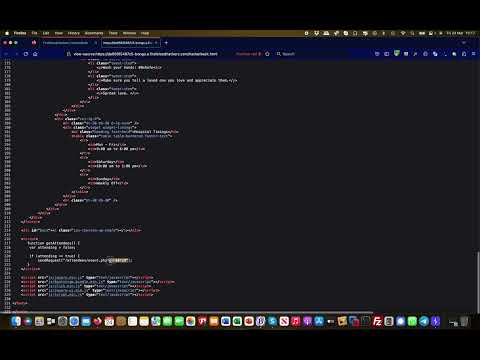
Account override Vulnerability | FirstBlood v1 | Bug Bounty ServiceПодробнее
