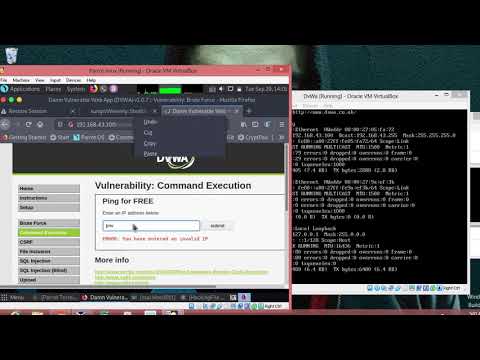
File upload vulnerabilities | Generating php payload using weevely

Exploit Basic File Upload Vulnerabilities to Hack Websites :- How to Use WeevelyПодробнее
File Upload Vulnerabilities to Hack Websites - Part 2 :- How to Use WeevelyПодробнее
Exploit File Upload Vulnerabilities to Hack Websites -Part 3 :- How to Use WeevelyПодробнее
Generating A PHP Backdoor with weevelyПодробнее

Kali Pen Test Lab - 5. Low Security Basic File Upload ExploitationПодробнее
Generating A PHP Backdoor with weevely Using Linux 2020Подробнее
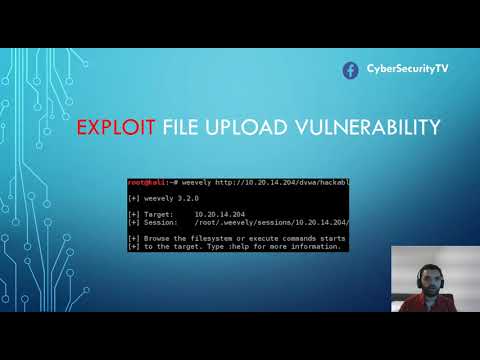
Exploit File Upload Vulnerability| WeevelyПодробнее
How Hackers Exploit PHP File Upload Vulnerabilities (Full Breakdown)Подробнее

Weevely PHP Backdoor | Web Hacking For Beginners | 2022Подробнее
Master in Hacking with Metasploit #78 Unrestricted file Uploading PHP payload MetasploitПодробнее

Creating a PHP Webshell using Weevely - Post ExploitationПодробнее

How to use Weevely PHP BackdoorПодробнее
PHP File Upload Vulnerability Explained (part 2)Подробнее

Generate PHP Web Shell Using WeevelyПодробнее
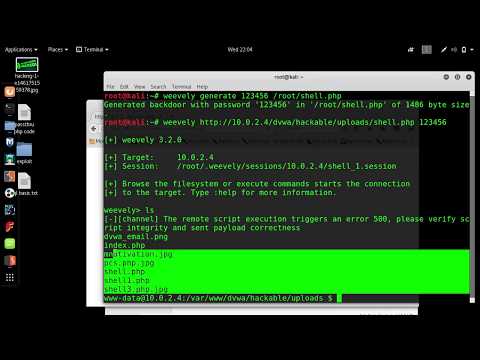
6. Weevely - How to Upload Files to Target Webserver | post exploitationПодробнее
WEBSITE HACKING DEMONSTRATION USING METASPLOITABLE ( Vulnerability: UPLOAD) USING WEEVELY TOOLПодробнее
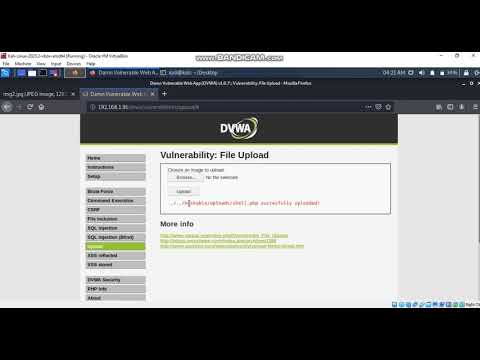
File Uploading Test and Exploit Using Weevely | #shorts #bugbountyПодробнее
Weevely hacking DVWAПодробнее