Exploring the Attack Surface
Far beyond the perimeter - exploring external attack surfacesПодробнее

Exploring Browser Extensions with John TucknerПодробнее

Exploring the latest FortiGuard Labs Threat Report - Derek Manky - ESW VaultПодробнее

Cloud Security Risks: Exploring the latest Threat Landscape ReportПодробнее

Exploring Quality Prompting Techniques in Copilot for SecurityПодробнее

Exploring the challenges of managing attack surfaces by P&P ElectronicsПодробнее

No Hat 2024 - Jacopo Jannone - Exploring and Exploiting an Android “Smart POS” Payment TerminalПодробнее

Exploring the Wiz Cloud Security PlatformПодробнее
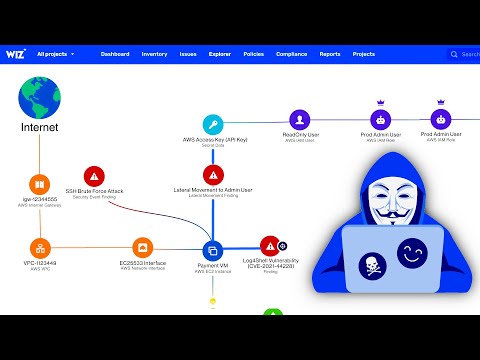
Exploring External Attack Surfaces for Initial Access in Microsoft Azure Cloud | CyberWarFare LabsПодробнее

Exploring the Complementary Nature of External Attack Surface Management in CybersecurityПодробнее

Explore Attack Surface Resilience: GigaOm Analyst Insights on ASMПодробнее

HackNotice at BlackHat 2023: Confronting the Missing Human Attack SurfaceПодробнее

What's New in Microsoft Defender for Cloud Container SecurityПодробнее

Exploring IoT and OT HackingПодробнее

Unveiling the Catalysts of Cybersecurity: Exploring Attack Surface ManagementПодробнее

The Most Dangerous Codec in the World: Finding and Exploiting Vulnerabilities in H.264 DecodersПодробнее

What's New in Microsoft Defender External Attack Surface ManagementПодробнее

The Next Big Thing: Exploring Cybersecurity with Ofer IsraeliПодробнее

Exploring the Attack Surface of Blockchain A Comprehensive SurveyПодробнее

The Pool Party You Will Never Forget: New Process Injection Techniques Using Windows Thread PoolsПодробнее
