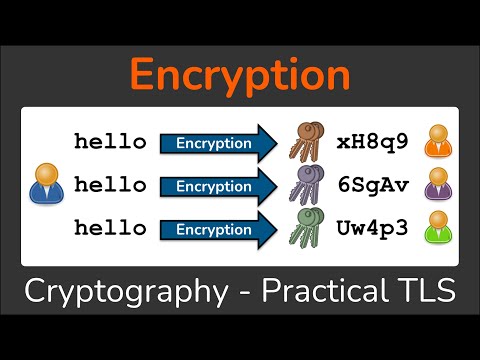
Encryption - Symmetric Encryption vs Asymmetric Encryption - Cryptography - Practical TLS
23. TLS Certificates in Kubernetes: A Practical GuideПодробнее

Elliptic Curve Cryptography in less than 5 minutesПодробнее

TLS 1.3 Cipher Suites - Here is what CHANGES!Подробнее

Mastering Cryptography: Security+ 701 Practice QuestionsПодробнее

TLS Handshake - EVERYTHING that happens when you visit an HTTPS websiteПодробнее

RSA & Asymmetric Encryption - Cryptography EssentialsПодробнее

SSL TLS Explained: How SSL Certificates & Encryption Keep Your Data Safe [HINDI]Подробнее
![SSL TLS Explained: How SSL Certificates & Encryption Keep Your Data Safe [HINDI]](https://img.youtube.com/vi/I43NnHTeACk/0.jpg)
A better definition of Asymmetric CryptographyПодробнее

SSL, TLS, HTTPS ExplainedПодробнее
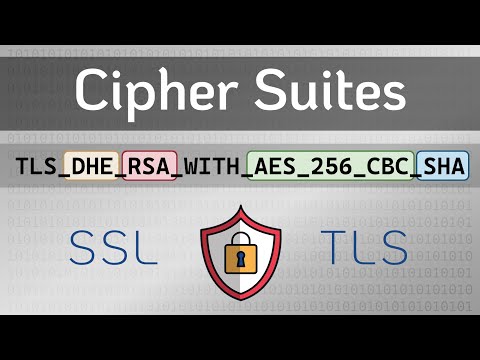
What are Cipher Suites? - Practical TLSПодробнее
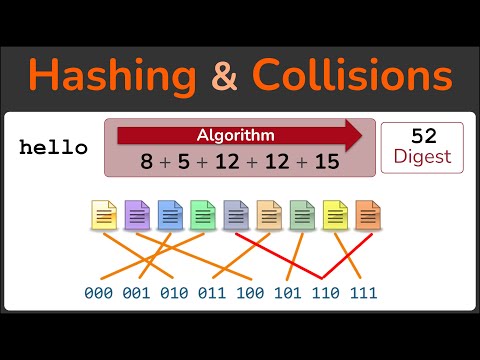
Hashing, Hashing Algorithms, and Collisions - Cryptography - Practical TLSПодробнее
Public and Private Keys - Signatures & Key Exchanges - Cryptography - Practical TLSПодробнее
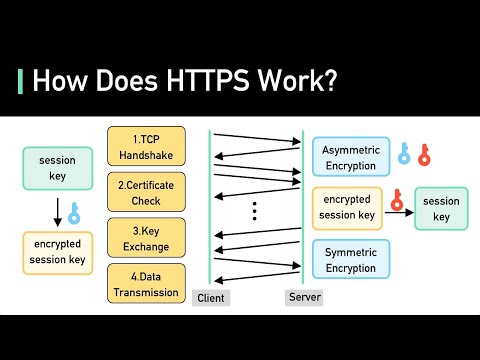
How SSL & TLS use Cryptographic tools to secure your data - Practical TLSПодробнее
Public Key Infrastructure - What is a PKI? - Cryptography - Practical TLSПодробнее

TLS Handshake Deep Dive and decryption with WiresharkПодробнее

Diffie-Hellman Key Exchange - the MAGIC that makes it possible - Cryptography - Practical TLSПодробнее
Data Integrity - How Hashing is used to ensure data isn't modified - HMAC - CryptographyПодробнее

RSA Algorithm - How does it work? - I'll PROVE it with an Example! -- Cryptography - Practical TLSПодробнее

TLS / SSL - The complete sequence - Practical TLSПодробнее
