Effectively use database import with Metasploit: Commands - hosts, services | importing scan results

Metasploit For Beginners - How To Scan And Pwn A Computer | Learn From A Pro HackerПодробнее
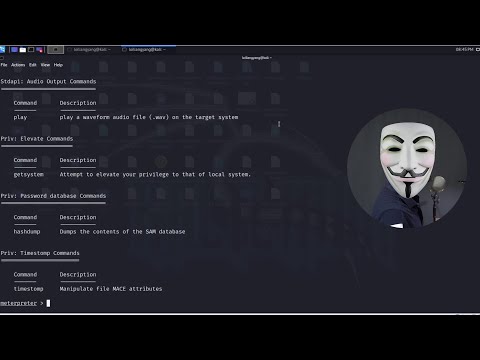
How to import modules into Metasploit - Resolving No results from searchПодробнее

Importing Nmap results into MetasploitПодробнее

Metasploit Tutorial for BeginnersПодробнее
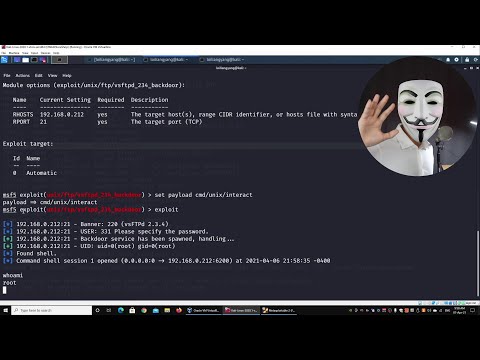
Importing a Nessus scan into MetasploitПодробнее

How to Add Modules to Metasploit // 2023 Ethical Hacking TutorialsПодробнее

Network Scanning Using Metasploit Framework (beginners)Подробнее

Access Android with Metasploit Kali (Cybersecurity)Подробнее
Hacking into Android in 32 seconds | HID attack | Metasploit | PIN brute force PoCПодробнее

how to get remote access to your hacking targets // reverse shells with netcat (Windows and Linux!!)Подробнее

Active Scanning with Metasploit PORTSCAN auxiliary module :TCP and SYN scans - Hands on with KaliПодробнее

Oracle Database Exploitation with Metasploit | CTF WalkthroughПодробнее

Metasploit tutorial |How to work with Databases in Metasploit?Подробнее

HACKERLOI.pdfПодробнее

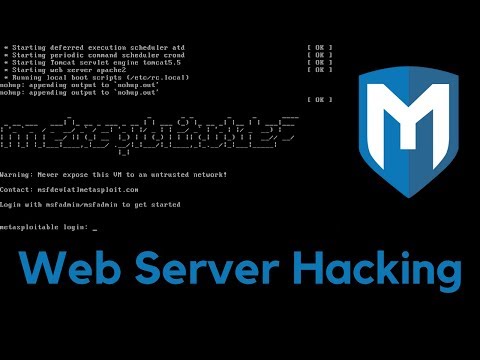
Gaining Access - Web Server Hacking - Metasploitable - #1Подробнее
How To Hack MySQL Using NMAP Scripts | Metasploitable 2Подробнее
METASPLOIT - HOW TO SCAN AND EXPLOIT A TARGETПодробнее
