Discover Juicy vulnerabilities using Burp Suite extensions - Content type Converter - Part 11

Discover Juicy Vulnerabilities using BurpSuite Extensions - Error Message Checks - Part 2Подробнее

Discover Juicy vulnerabilities using Burp Suite extensions - Reflected Parameters - Part 10Подробнее

Discover Juicy vulnerabilities using Burp Suite extensions - 401/403 Bypass Techniques - Part 13Подробнее

Discover Juicy vulnerabilities using Burp Suite Extensions - Upload Scanner - Part 16 | Cyber AdamПодробнее

Converting Content To and Between JSON and XML in Burp Suite Using Content Type ConverterПодробнее

Discover Juicy Vulnerabilities Using BurpSuite Extensions - Additional CORS Checks - Part 4Подробнее

Discover Juicy vulnerabilities using Burp Suite extensions - JS Link Finder & JS Miner - Part 9Подробнее

Discover Juicy vulnerabilities using Burp Suite extensions - Autorize - Part 7Подробнее

Discover Juicy vulnerabilities using Burp Suite extensions - Auth Matrix - Part 8Подробнее

Discover Juicy Vulnerabilities using Burpsuite Extensions - Active Scan ++ | Part 1 | Cyber AdamПодробнее

How to use Burp Suite for Spidering and Forced BrowsingПодробнее

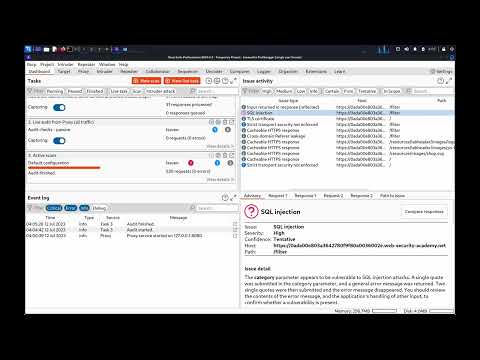
Testing for SQL injection vulnerabilities with Burp SuiteПодробнее
PortSwigger Lab 2: Unprotected admin functionality with unpredictable URL [Burmese]Подробнее
![PortSwigger Lab 2: Unprotected admin functionality with unpredictable URL [Burmese]](https://img.youtube.com/vi/mdzS9fXoUSA/0.jpg)
Discover Juicy vulnerabilities using Burp Suite extensions - Cloud Storage Tester- Part 14Подробнее

Discover Juicy vulnerabilities using Burp Suite Extensions - J2EE Scan - Part 17 | Cyber AdamПодробнее

BurpSuite | #11 Various Injection Vulnerability Attacks |BugBountyHunting,WebHacking|Premium PiratesПодробнее

00034 4 8Introducing the Burp Suite: The Ultimate Tool for Web Application Security TestingПодробнее

Discover Juicy Vulnerabilities Using BurpSuite Extensions - Collaborator Everywhere - Part 3Подробнее
