Cross site scripting (XSS) Vulnerability | POC | Hackerone | Bugcrowd | Bug bounty |
🛠 Demo Zendesk Stored XSS Vulnerability in File Upload System | Real World | Bug Bounty POCПодробнее

Live Bug Hunting Active HackerOne & BugCrowd Domains Private Methodology | 2025Подробнее
Paypal - Live bug bounty hunting on Hackerone | Live Recon | part 1 | For Beginners | 2025Подробнее
Live Bug Bounty Hunting: The Ultimate Checklist to Level Up Your Skills | Bugcrowd | part-(1)Подробнее
Open redirect Bug report Poc video #bugbounty #hackingcommunity #hacker #hackerone #bugcrowdПодробнее
"XSS Bug Bounty Hunting : How to Find & Exploit Cross-Site Scripting (POC) | Ethical Hacking Guide"Подробнее
HTML Injection to Open Redirect Bug POC | Bug Bounty | #bugbounty #hackerone #pentestingПодробнее
How to Access 404 Files Of Any Server | Bug Bounty POC | Live Recon | part 2 | ROPПодробнее

🚀 Automated XSS Methodology for Bug Bounty Hunters #bugbounty #bugbountytipsПодробнее
🚀 Automated XSS Methodology for Bug Bounty Hunters | xss0r ToolПодробнее
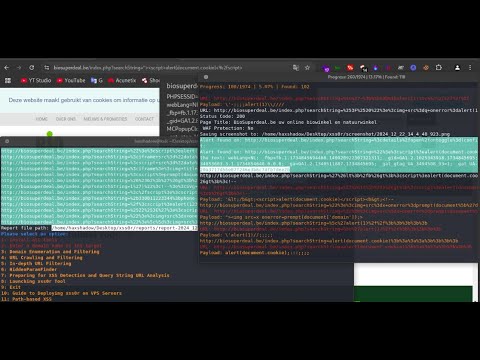
Hidden secrets and urls in JS Mass hunting || Bug bounty POCПодробнее

Forced Tampering leads to Admin panel access | Bug Bounty POC | Lazy PentesterПодробнее
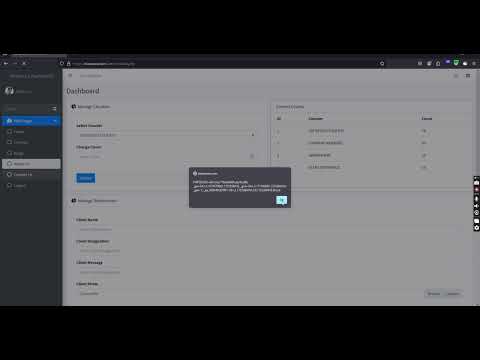
LFI and XSS Vulnerabilities Explained | Bug Bounty Hunting Made EasyПодробнее
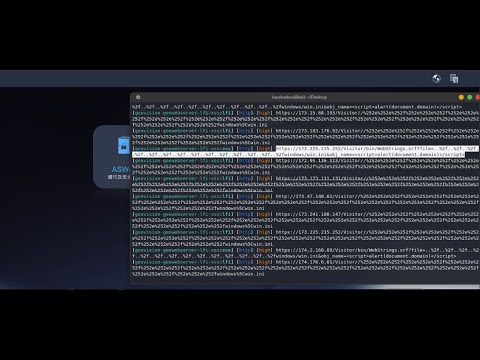
Easy way to Find LFI cve+manually+Automation | Bug bounty pocПодробнее
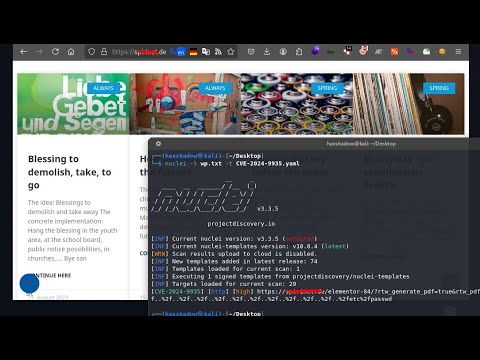
XSS Methodology for Bug Bounty Hunters | WordPress GuideПодробнее
OWASP Top 10 Vulnerabilities Explained | Marathi Bug Bounty Series Day #2Подробнее

Bug Bounty Basics: Your Guide to Starting in Ethical HackingПодробнее

Stored XSS | Bug Bounty POCПодробнее
Open Redirect in 404 Page | bug bounty POC 🔥Подробнее

Proven XSS Methodology for Bug Bounty Hunters | WordPress GuideПодробнее