Cross Site Request Forgery (CSRF) | Owasp Top 10 Explainer Video | Secure Code Warrior

Insecure Deserialization | Owasp Top 10 Explainer Video | Secure Code WarriorПодробнее

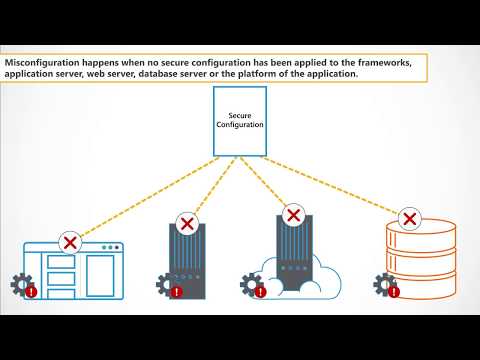
Security Misconfiguration | Owasp Top 10 Explainer Video | Secure Code WarriorПодробнее
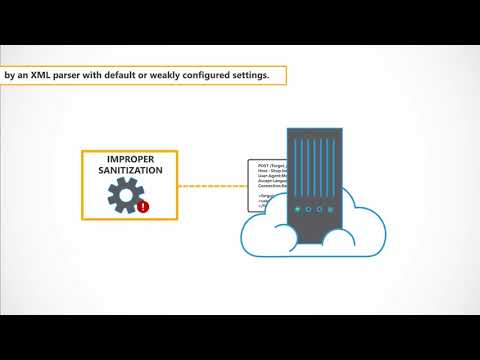
XML External Entities (XXE) | Owasp Top 10 Explainer Video | Secure Code WarriorПодробнее
CRLF Injection | OWASP Top 10 Explainer Video | Secure Code WarriorПодробнее

Using Components with Known Vulnerabilities | Owasp Top 10 Explainer Video | Secure Code WarriorПодробнее

Session Management Weaknesses | Owasp Top 10 Explainer Video | Secure Code WarriorПодробнее

Cross-Site Scripting (XSS) | Owasp Top 10 Explainer Video | Secure Code WarriorПодробнее
Broken Authentication | Owasp Top 10 Explainer Video | Secure Code WarriorПодробнее
OS Command Injections | Owasp Top 10 Explainer Video | Secure Code WarriorПодробнее

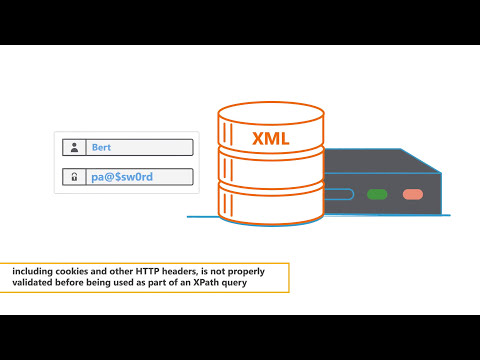
XPath & XML Injections | Owasp Top 10 Explainer Video | Secure Code WarriorПодробнее