Collisions for MD5 and SHA-1

Can hash algorithm such as MD5/SHA-1 generate an ID with less probability of collision than pure ...Подробнее
What Is Hashing? | Hashing Explained With Example | Hashing Practical Demonstration | SimpilearnПодробнее

MD5 vs. SHA-1 in PHP | Complete PHP Course on YouTubeПодробнее

Can hash algorithm such as MD5/SHA-1 generate an ID with less probability of collision than pure ranПодробнее

Can hash algorithm such as MD5/SHA-1 generate an ID with less probability of collision than pure ranПодробнее

MD4, MD5, SHA-0, SHA-1, SHA-2, RIPEMDПодробнее

MD5 & SHA – A NOTEПодробнее

MD4, MD5, SHA1, SHA2, SHA3 in Network SecurityПодробнее

MD4, MD5, SHA1, RIPEMD, SHA2, and SHA3Подробнее

LAB 2 - MD5 Collision Attack Lab - (من المهمة 1 إلى 4) - الأستاذ حسن فهد السلطانПодробнее

Hashing, Hashing Algorithms, and Collisions - Cryptography - Practical TLSПодробнее
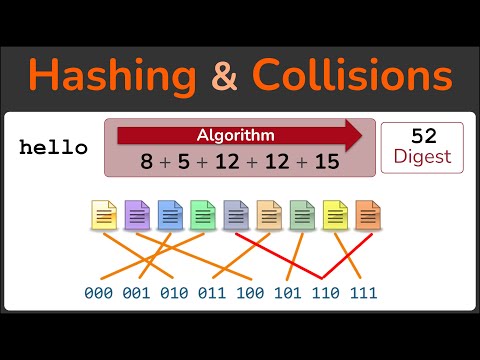
MD5 Hash CollisionПодробнее

11 Cryptographic Hash Function and its Properties: Pre-image, Second Pre-image, Collision ResistanceПодробнее

Cryptography with Python 26: Using MD5, SHA-1, SHA-2, SHA-3 in PythonПодробнее

MD4, MD5, SHA1, RIPEMD, SHA2Подробнее

Class4crypt c4c7.4 Colisiones en funciones hash MD5 y SHA-1Подробнее

Explanation of Cybersecurity Hashing and MD5 CollisionsПодробнее

Top Hashing Algorithms In Cryptography | MD5 and SHA 256 Algorithms Explained | SimplilearnПодробнее

Cryptography with Python 25: Hash function securityПодробнее
