bWAPP Broken Authentication - CAPTCHA Bypassing | (Low,Medium,High)

A2 Broken Authentication - Weak Passwords | Level Low Medium HighПодробнее

Broken Auth Logout Management Low Security LevelПодробнее

Broken Auth. - CAPTCHA BypassingПодробнее

bwapp broken authentication captcha bypassing || bwapp broken authentication || Cyber World HindiПодробнее

Broken Auth CAPTCHA Bypassing Low Security LevelПодробнее
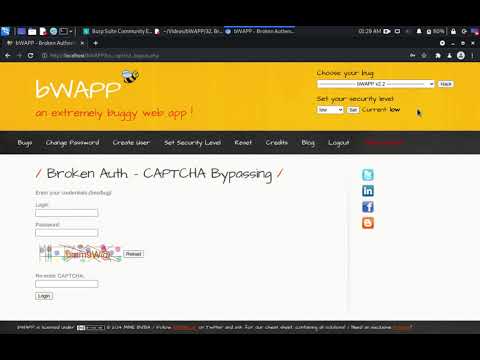
bWAPP - Broken Auth - CAPTCHA Bypass (High Security Level)Подробнее

A2 Broken Authentication - Capcha Bypassing | Level LowПодробнее

bWAPP Broken Authentication Login Forms and Logout ManagementПодробнее

Captcha Bypass || POC || Bug Bounty || Mr. Kunj Patel (Legacy_Defender)Подробнее

A2 Broken Authentication - Password Attacks | Level LowПодробнее

bWAPP full solutionsA2 Broken Authentication and Session ManagementПодробнее

웹해킹 30. A2 - bWAPP Broken Authentication - CAPTCHA BypassingПодробнее

46_Broken Auth - Forgotten FunctionПодробнее

6 Authentication Bypass Exploitation CaptchaПодробнее

Broken Auth Weak Passwords Low Security LevelПодробнее

Authentication Bypass via Response manipulation Vulnerability Live Website #Bugbounty #POC || 2022Подробнее