Attack Windows 11 with Trojan file (Metasploit Framework)

CREATING WINDOWS PAYLOAD WITH MSFVENOM | METASPLOIT PENETRATION TESTING | 2023Подробнее

How to Generate Windows Backdoors with Metasploit FrameworkПодробнее

Metasploit For Beginners - How To Scan And Pwn A Computer | Learn From A Pro HackerПодробнее
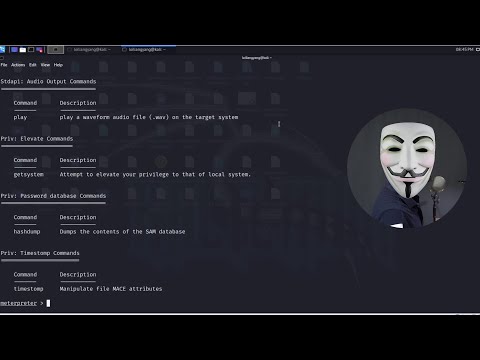
Bypassing a FULLY Patched Windows 11 + Defender with a Meterpreter Shell Using ScareCrow!Подробнее

HAVOC C2 - Demon Bypasses Windows 11 DefenderПодробнее

Hacking into Android in 32 seconds | HID attack | Metasploit | PIN brute force PoCПодробнее

Windows has a hidden malware removal tool | #shorts #trending #mrt #malwareПодробнее
Metasploit Tutorial for BeginnersПодробнее
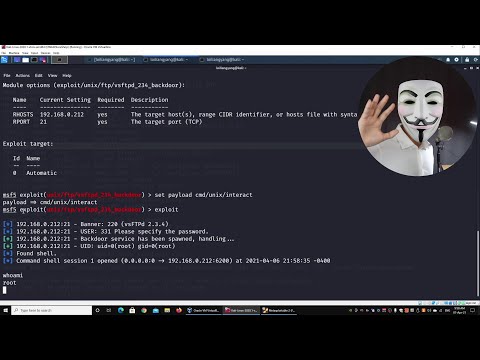
Exploiting Windows 10 | Kali Linux - Windows | LabПодробнее

How to Create Trojans Using PowershellПодробнее

Metasploit Windows Attack TutorialПодробнее

How to install the Metasploit framework on Windows 11 - EDUCATIONAL PURPOSESПодробнее

Use Msfvenom to Create a Reverse TCP PayloadПодробнее

How to Remove Trojan Virus from Windows?Подробнее
how to create a trojan with image file? - create backdoor trojanПодробнее

how to get remote access to your hacking targets // reverse shells with netcat (Windows and Linux!!)Подробнее

When you first time install Kali linux for hacking 😄😄 #hacker #shortsПодробнее

Create windows backdoor using metasploit in kali linux | CEHv11Подробнее
