Asymmetric Key Cryptography in Cyber Security with Solved examples | असममित कुंजी क्रिप्टोग्राफी

Symmetric Key Cryptography with Solved Examples | नेटवर्क सुरक्षा में सममित कुंजी क्रिप्टोग्राफीПодробнее

RSA and DSA Encryption Algorithms Explained | Cryptography & Network Security Tutorial | SimplilearnПодробнее

Asymmetric key Cryptography | Asymmetric key encryptionПодробнее

Cryptography Full Course | Cryptography And Network Security | Cryptography | SimplilearnПодробнее

Types of Encryption | Symmetric Key and Asymmetric Key EncryptionПодробнее

Symmetric Key Cryptography And Asymmetric Key Cryptography | Cryptography Tutorial | SimplilearnПодробнее

Remote User Authentication using Asymmetric Encryption in Network Security | Woo and Lam ProposalПодробнее

Cryptography (Solved Questions)Подробнее

Stanford CS105: Introduction to Computers | 2021 | Lecture 20.2 Computer Security: MechanismsПодробнее

DSA Algorithm | DSA Algorithm Explained | Digital Signature Algorithm | SimplilearnПодробнее

How symmetric and asymmetric encryption and digital signatures workПодробнее
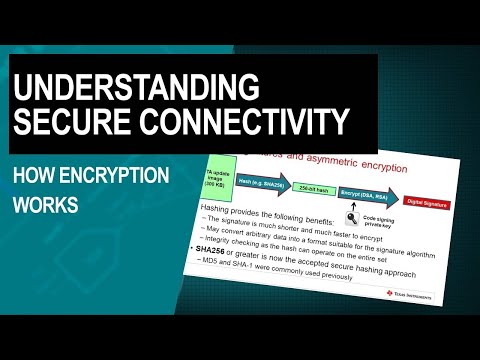
CISSP Domain 3 Review / Mind Map (6 of 9) | CryptographyПодробнее

Asymmetric Key CryptographyПодробнее

Asymmetric Key Cryptography | RSA Encryption Algorithm | Asymmetric Encryption | SimplilearnПодробнее

Trapdoor Function in Asymmetric Key Cryptography - | Information Security Lectures HindiПодробнее

Symmetric Key Cryptography | Stream Cipher & Block Cipher Explained | Network Security | SimplilearnПодробнее
CryptographyПодробнее

Asymmetric Key Cryptography ll Information and Cyber Security Course Explained in HindiПодробнее
