A9 Using Known Vulnerable Components - Buffer Overflow (Remote)

A9 Using Known Vulnerable Components - Buffer Overflow (Local)Подробнее

A9 Using Known Vulnerable Components - Shellshock Vulnerability CGIПодробнее

A9 Using Known Vulnerable Components - phpMyAdmin BBCode Tag XSSПодробнее

Buffer OverflowПодробнее

웹해킹 106. A9 - bWAPP Using Known Vulnerable Components - PHP CGI Remote Code ExecutionПодробнее

웹해킹 102. A9 - bWAPP Using Known Vulnerable Components - Buffer Overflow(Local)Подробнее

웹해킹 103. A9 - bWAPP Using Known Vulnerable Components - Buffer Overflow(Remote)Подробнее

How to hack back to the basic (Remote buffer overflow)Подробнее
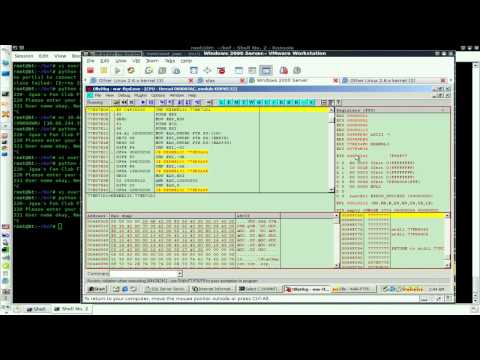
Remote Buffer OverflowПодробнее

Intel/Phoenix SecureCore: unsafe UEFI variable handling (CVE-2024-0762) #shorts #breakingПодробнее

Cloudme Sync 1.9.2 Remote Buffer Overflow DemoПодробнее
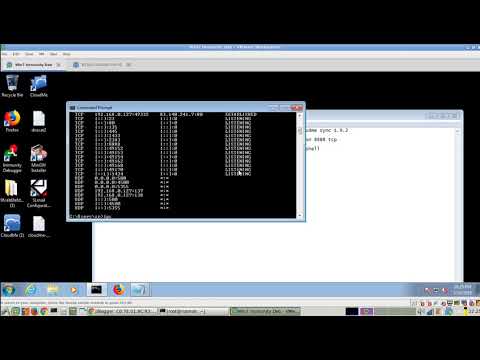
buffer overflow in web application hacking in owaspbwa and webgoatПодробнее

How to exploit a buffer overflow vulnerability - PracticalПодробнее
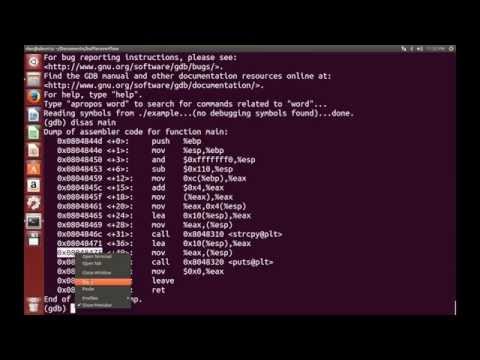
웹해킹 109. A9 - bWAPP Using Known Vulnerable Components - Shellshock Vulnerability(CGI)Подробнее

Hacker Course - Remote buffer overflow tutorial (Advanced)Подробнее
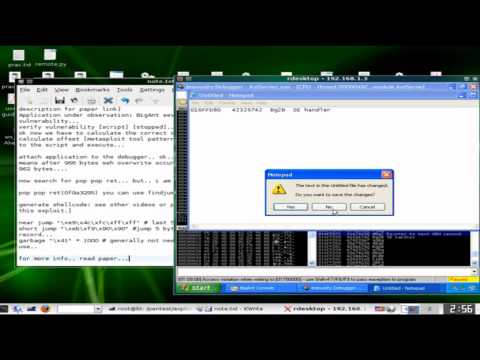
What is buffer overflow in hacking #cybersecurity #ethicalhacking #exploit #internshipПодробнее

Remote buffer overflow tutorial (credits D0uBle ZerO Zer0)Подробнее
Remote Buffer OverFlow P22 and Windows Privilege Escalation | CTF WalkthroughПодробнее

웹해킹 105. A9 - bWAPP Using Known Vulnerable Components - Heartbleed VulnerabilityПодробнее
